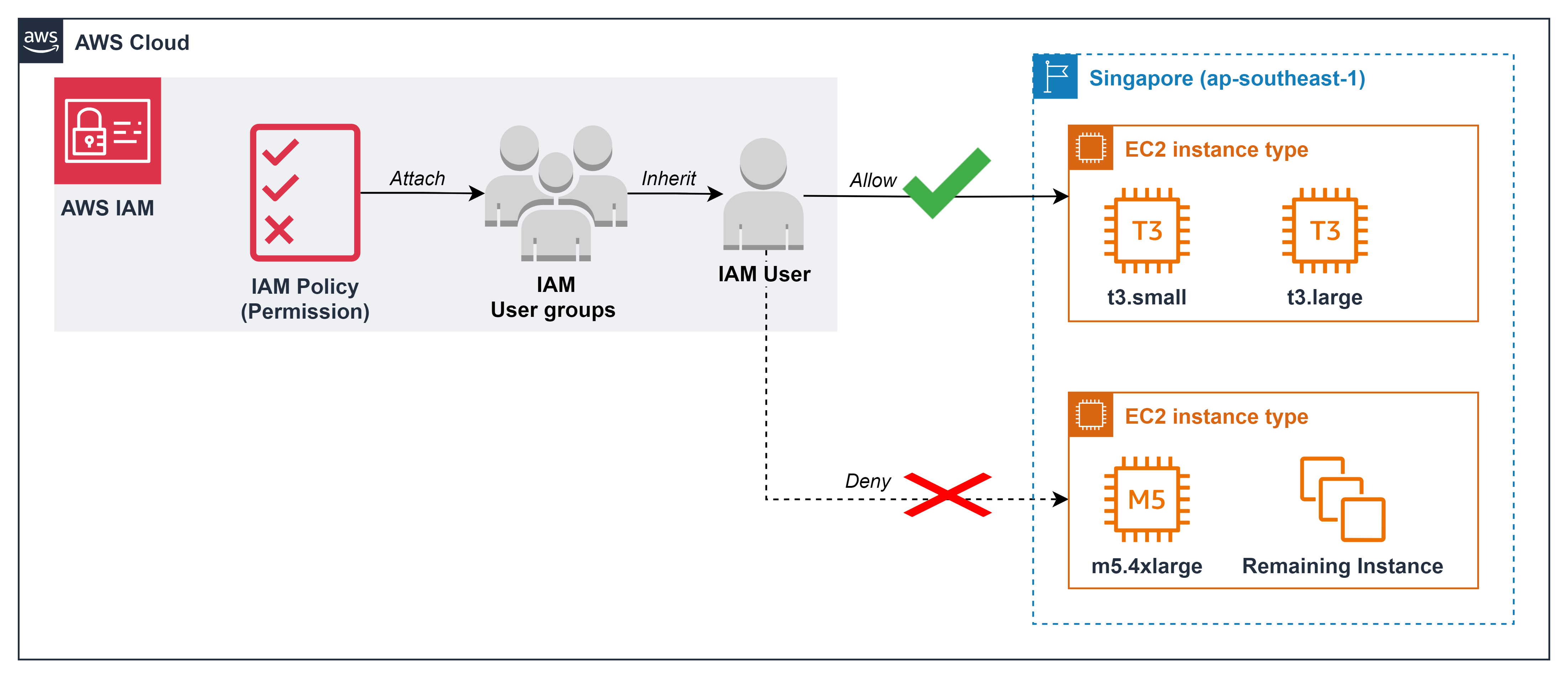
Limit EC2 usage by Instance type
Limit EC2 usage by Instance Type
-
Suppose, after a period of monitoring EC2 for the dev/test environment - you are allowed to create Instance Families: T3, T4g, M5! You see that the dev team often uses Instance Family as T3 with Instance Type as t3.small and t3.large.
-
After meeting with the Tech lead, in the spirit of cost optimization with least-privilege permissions, you continue to create a new Permissions policies for the dev/test environment, avoiding the human-error in creating instances with configurations like m5.4xlarge(16 vCPU, 64 GiB ram) may be without using up all the performance - causing waste.
-
Create an IAM Policy that only allows users to initialize EC2 with instance types: t3.small and t3.large
- In the AWS console, in the search box, enter
IAM - Select IAM service
- On the left side of the screen, select
Policies - Select Create policy
- Create policy in JSON data format instead of Visual. Select
JSON
- Scan the entire current code and press the Delete button
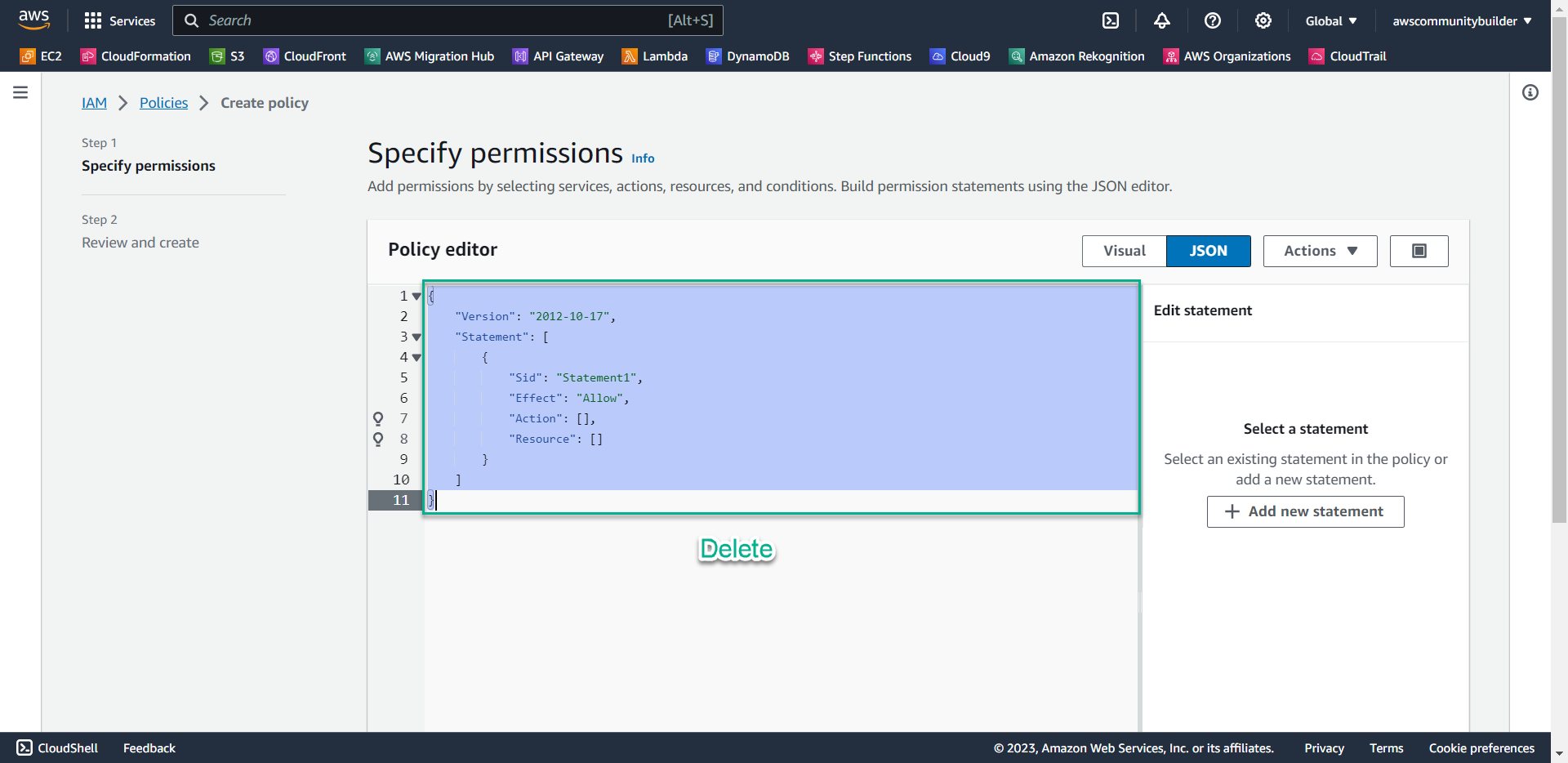
- Copy the following code into the Policy editor box, scroll down and select Next
- Meaning: User has the right to create EC2 with instance type: t3.small and t3.large
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": "ec2:*", "Resource": "*" }, { "Effect": "Deny", "Action": "ec2:RunInstances", "Resource": "arn:aws:ec2:*:148922931563:instance/*", "Condition": { "StringNotLike": { "ec2:InstanceType": [ "t3.small", "t3.large" ] } } } ] }- Noted: in the Resource line, replace the 12-digit sequence with your AWS account ID. Select the triangle symbol, then select the square symbol to copy the AWS account ID
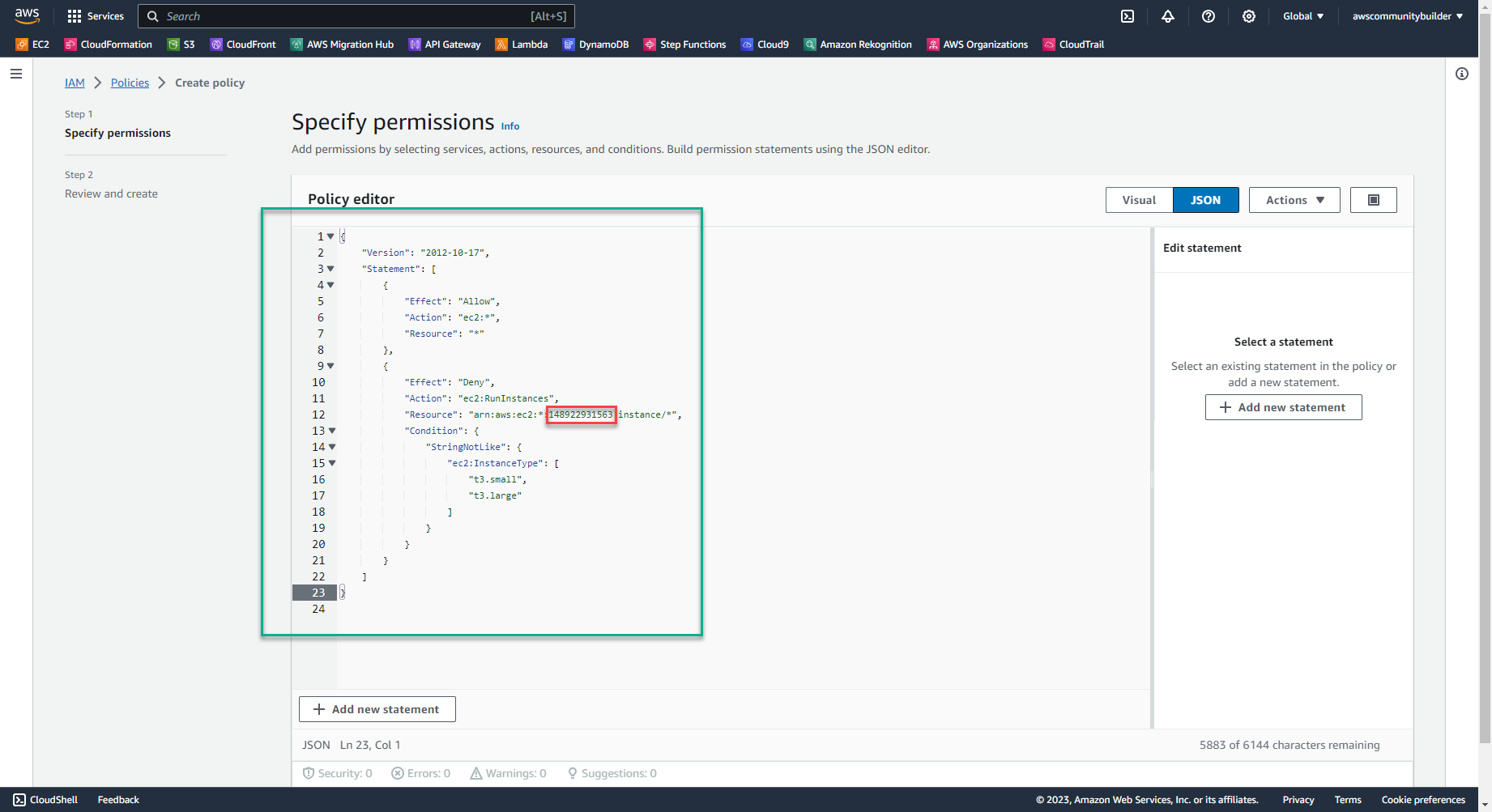
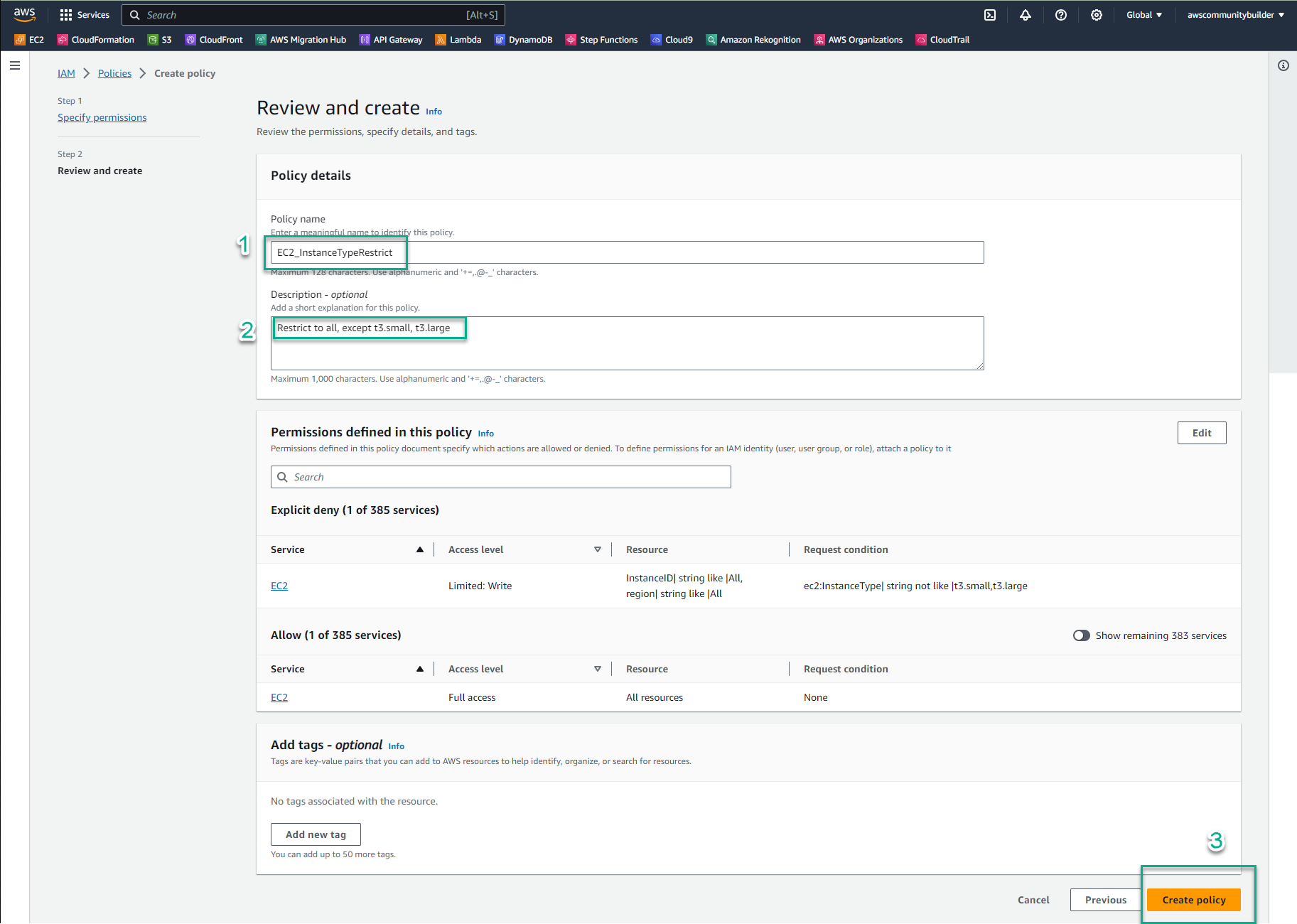
- In the Policy name section, enter:
EC2_InstanceTypeRestrict - In the Description section, enter:
Restrict to all, except t3.small & t3.large - Scroll to the bottom of the page and select Create policy
- In the AWS console, in the search box, enter
-
Add policy EC2_InstanceTypeRestrict to group CostTest
- At IAM Console, left section - select User groups
- Select CostTest
- Select Permissions
- Select Add permissions, select Attach policies
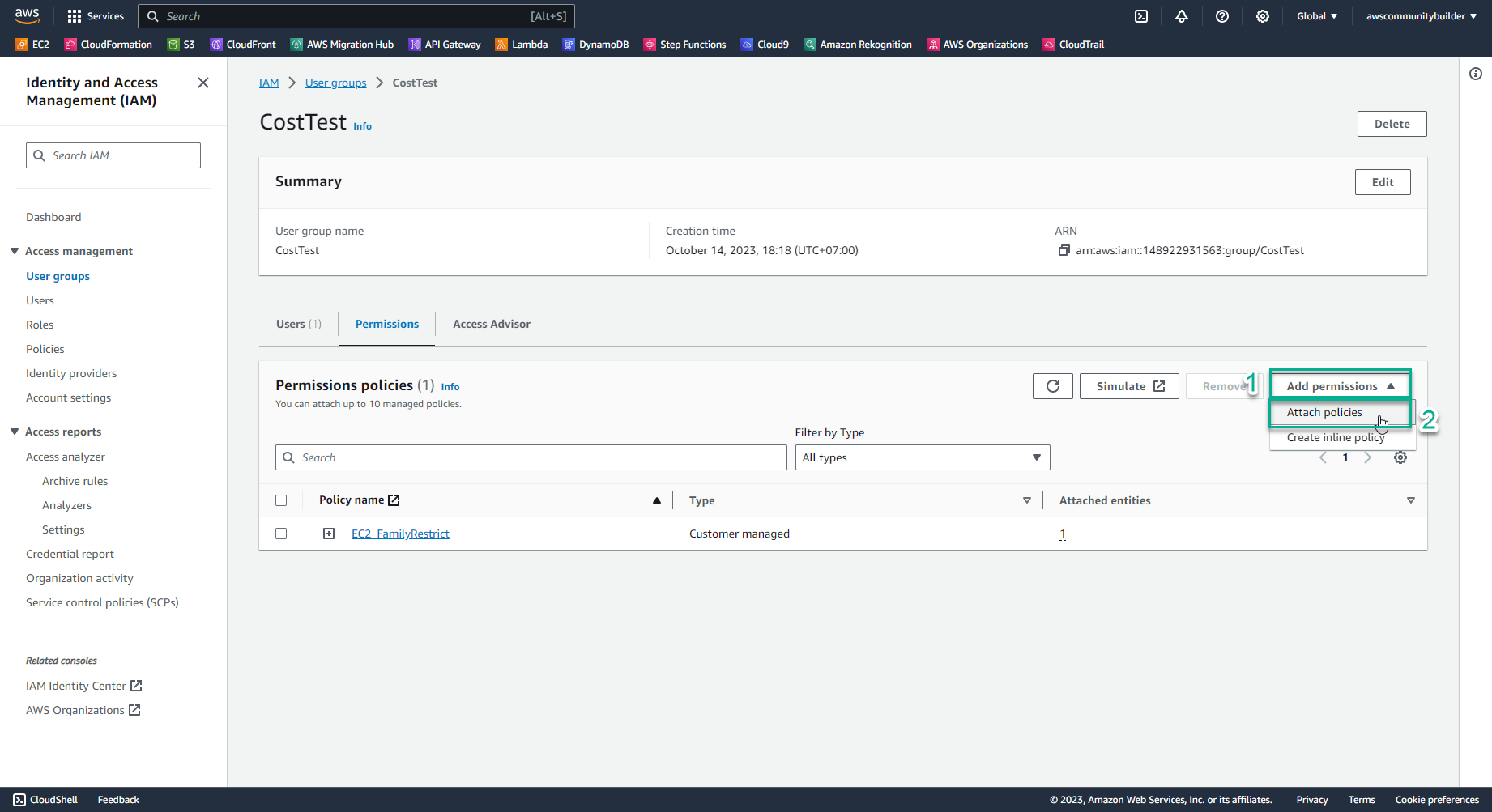
- In the search box 🔍, enter
EC2_InstanceTypeRestrict. - Check the box symbol □ to select a policy, select Attach policies
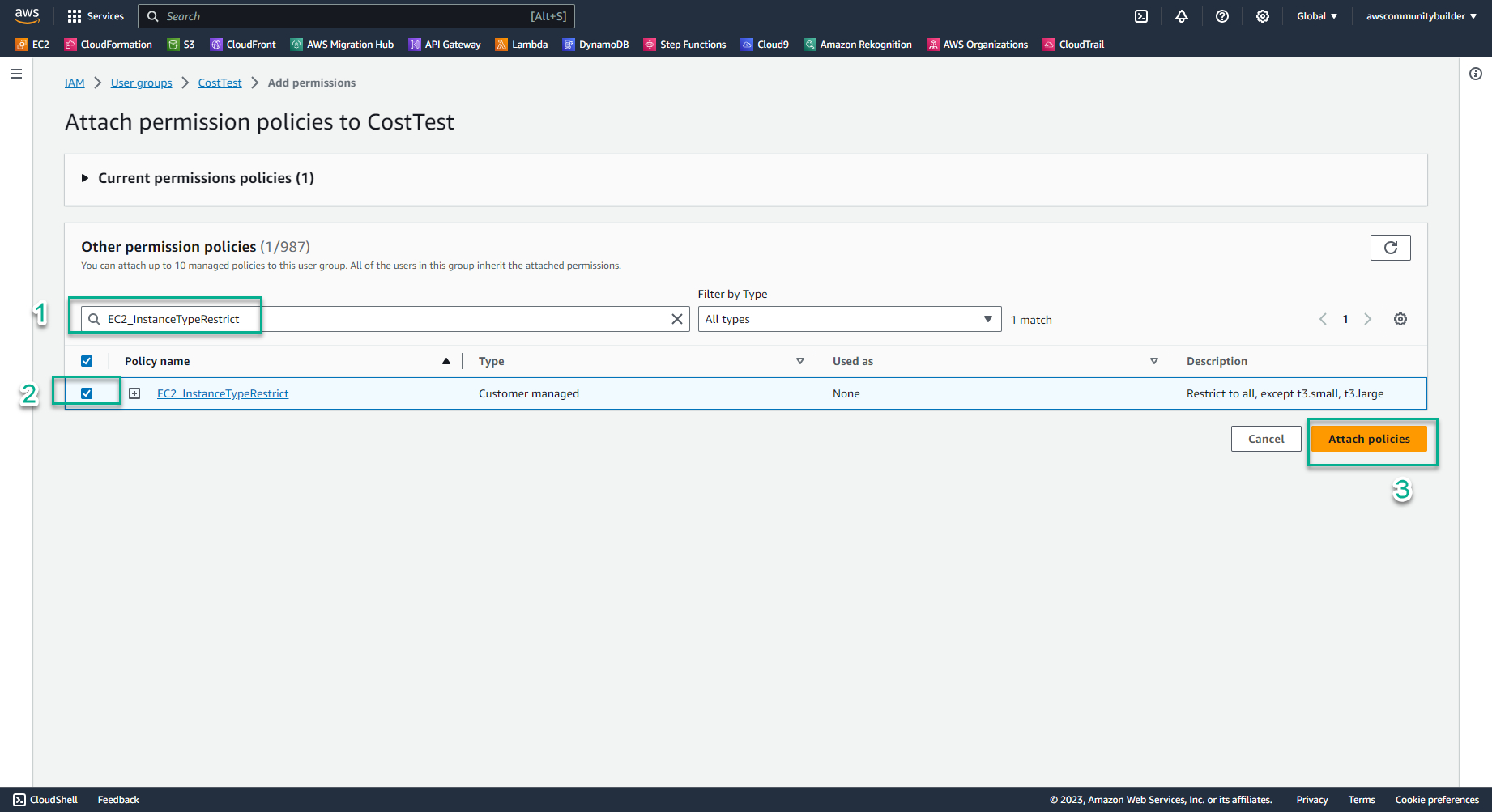
- Check Permissions policies
- Now in the CostTest group there is policy EC2_InstanceTypeRestrict and policy EC2_FamilyRestrict that you created in lab 8.2
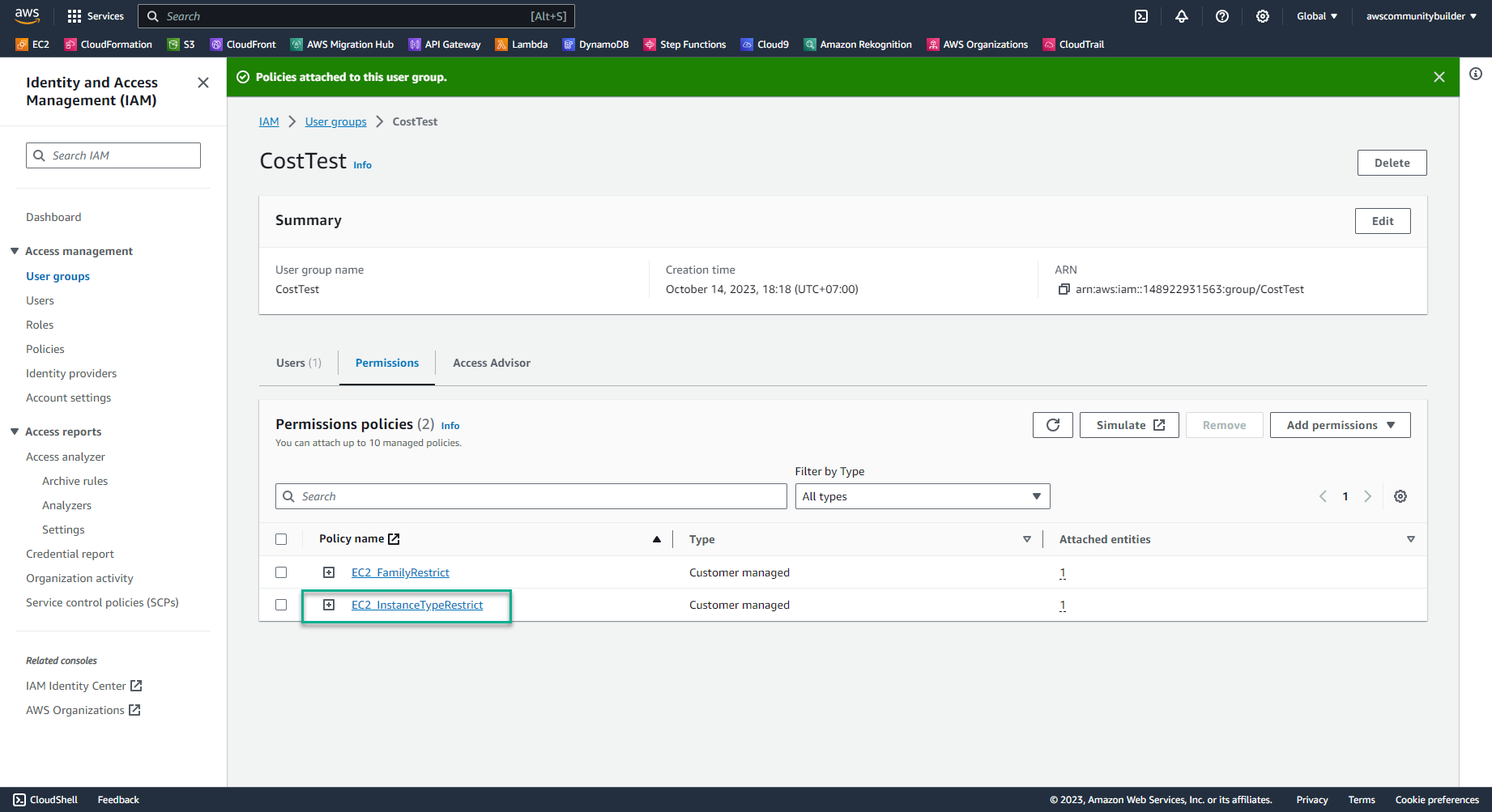
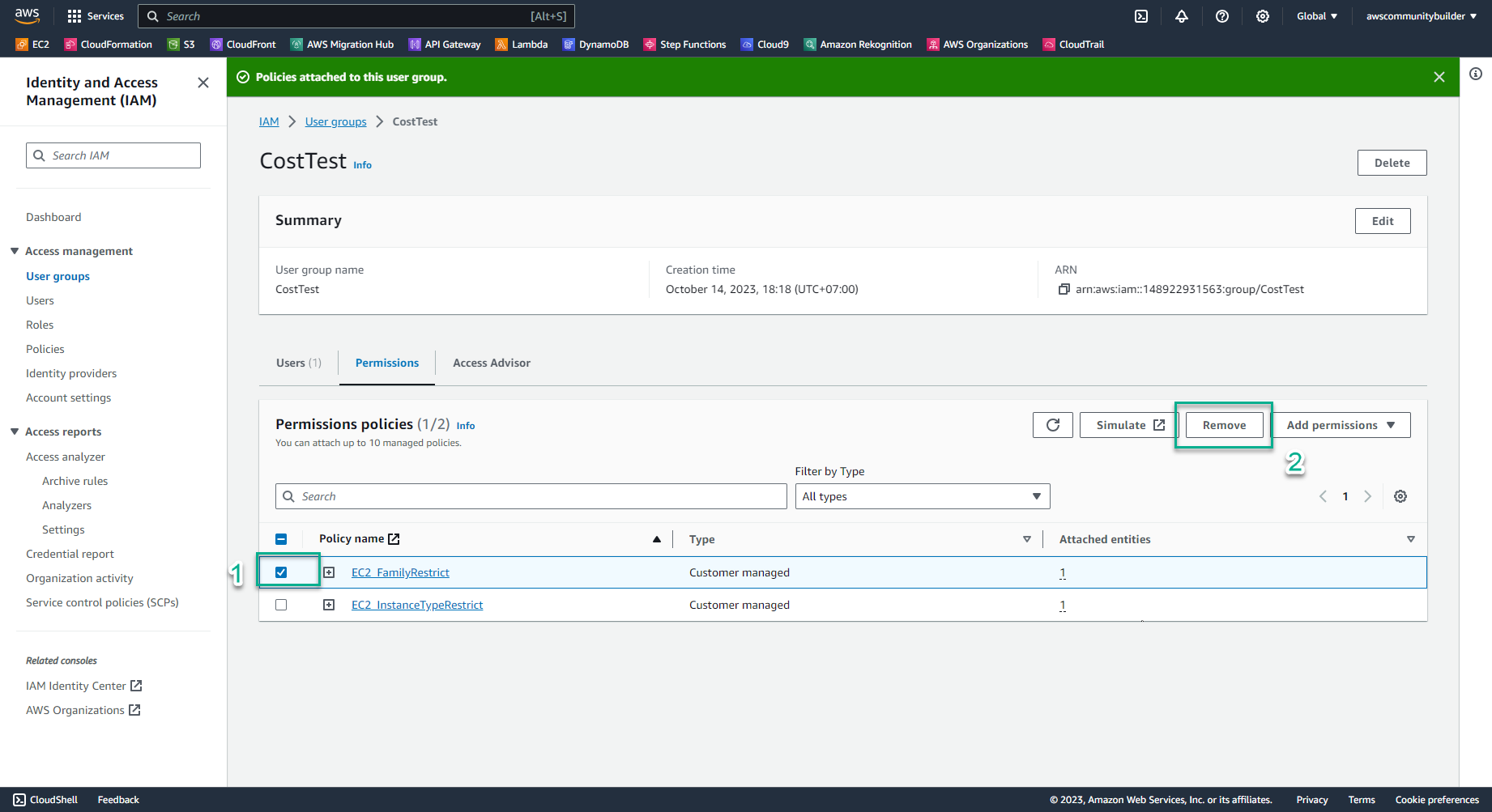
- Remove policy EC2_FamilyRestrict because of least-privilege permissions criteria
- Check the box symbol □ to select the policy, select Remove
-
Check User’s policy
- Select Users
- Select TestUser
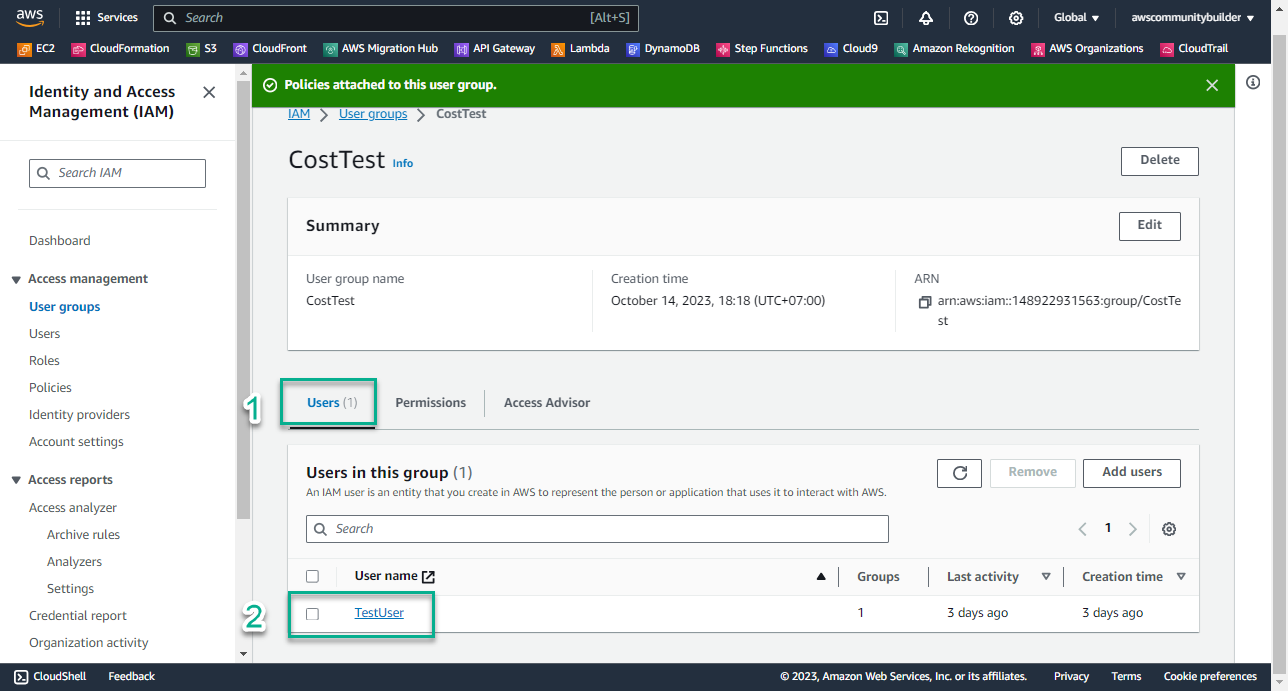
-
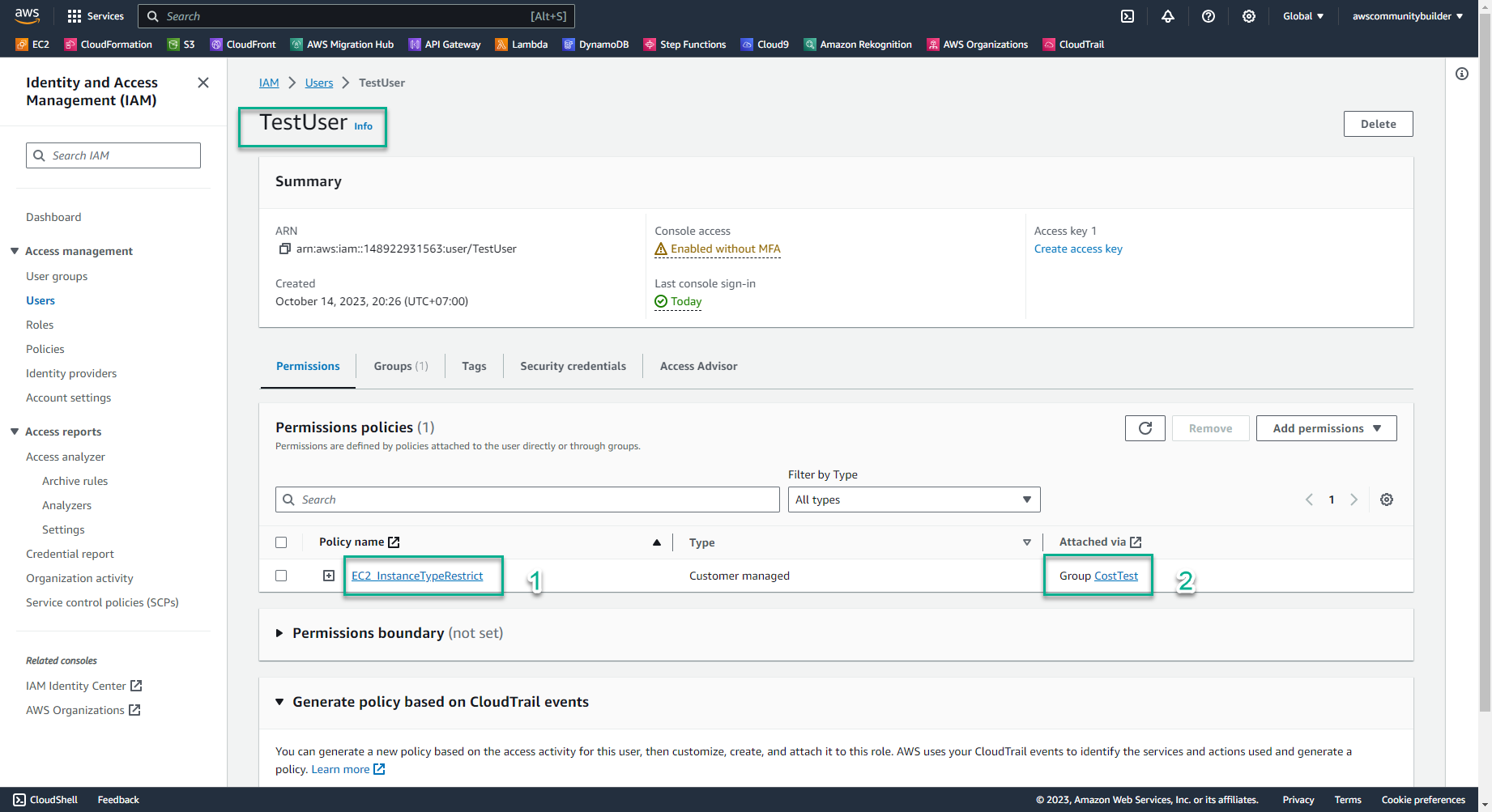
At this time, at IAM User: TestUser, in the Policy Name section you see the appearance of the policy EC2_InstanceTypeRestrict
-
In the section Attached via - Group CostTest, it means that these policies are assigned to the User through the group, not directly to the User.
-
-> This satisfies AWS’s best practice of centralized rights management through Group
-
Check Permissions policies for Instance Type: t3.small
- Log in to TestUser with the information you created in lab 8.1, step 4
- Make sure you are in Region Singapore
- In the search box 🔍, enter
EC2
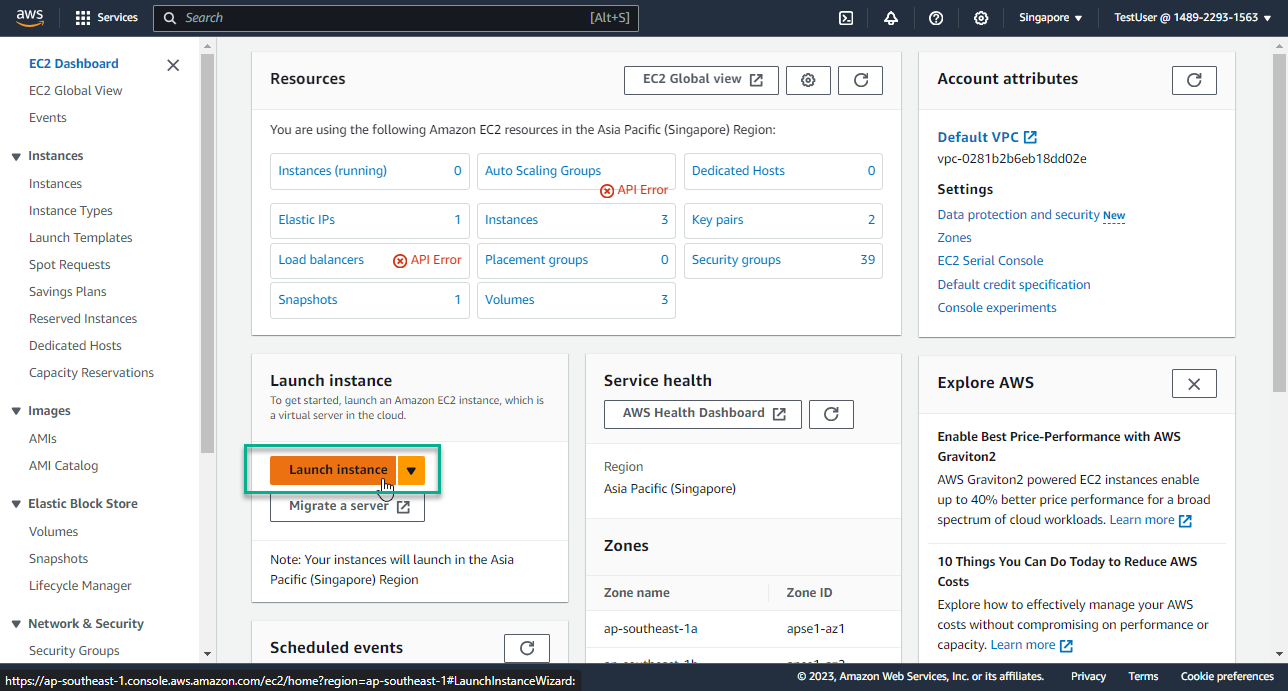
- At the EC2 interface, in the middle of the page, select Launch instance
-
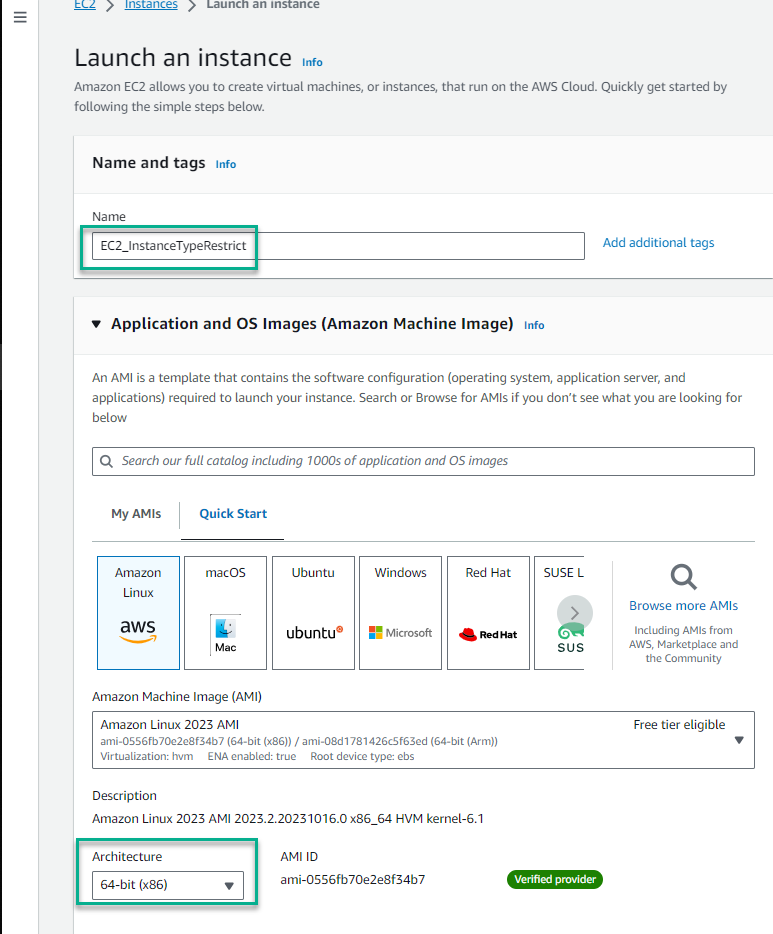
In the Name section, enter
EC2_InstanceTypeRestrict -
In the Architecture section, keep the value 64-bit (x86)
- In the Instance type section, select the triangle symbol, enter
t3.small
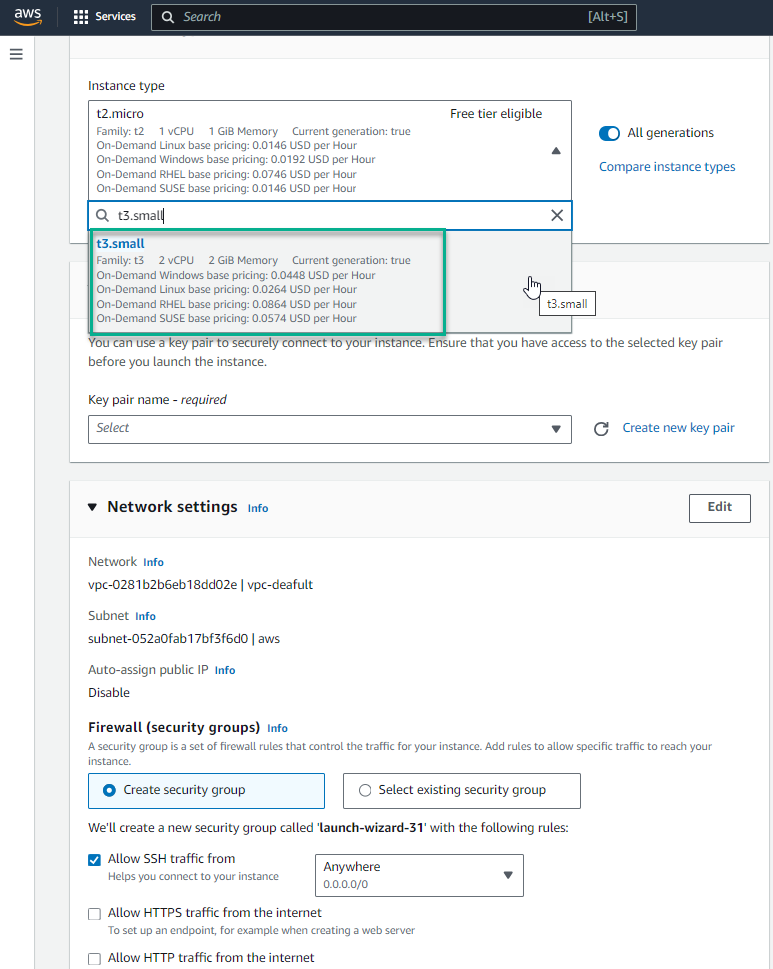
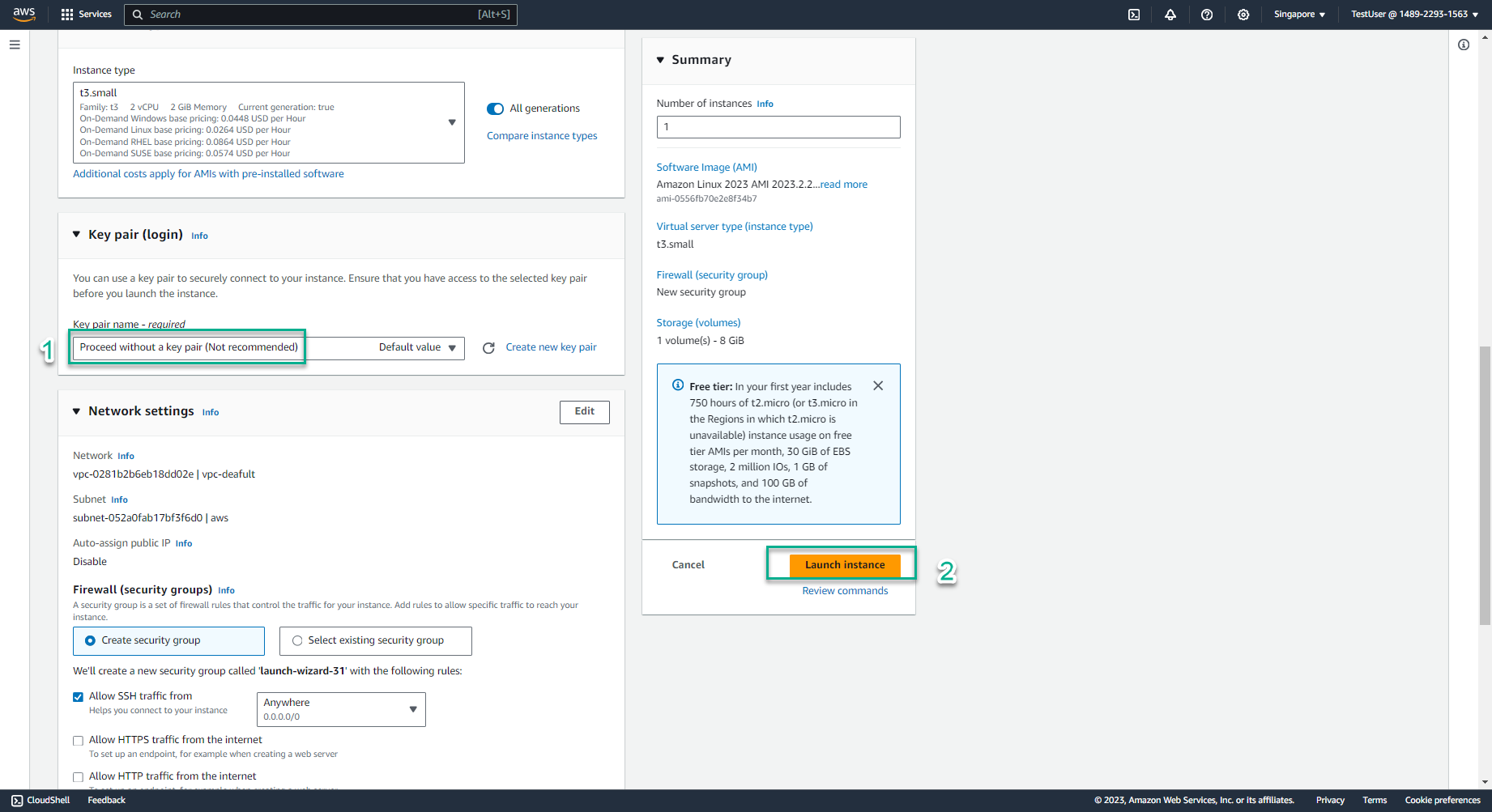
- In the key pair name section, select the triangle symbol, select Proceed without a key pair (Not recommended)
- Select Launch instance
- Select Instance ID that has just been successfully created
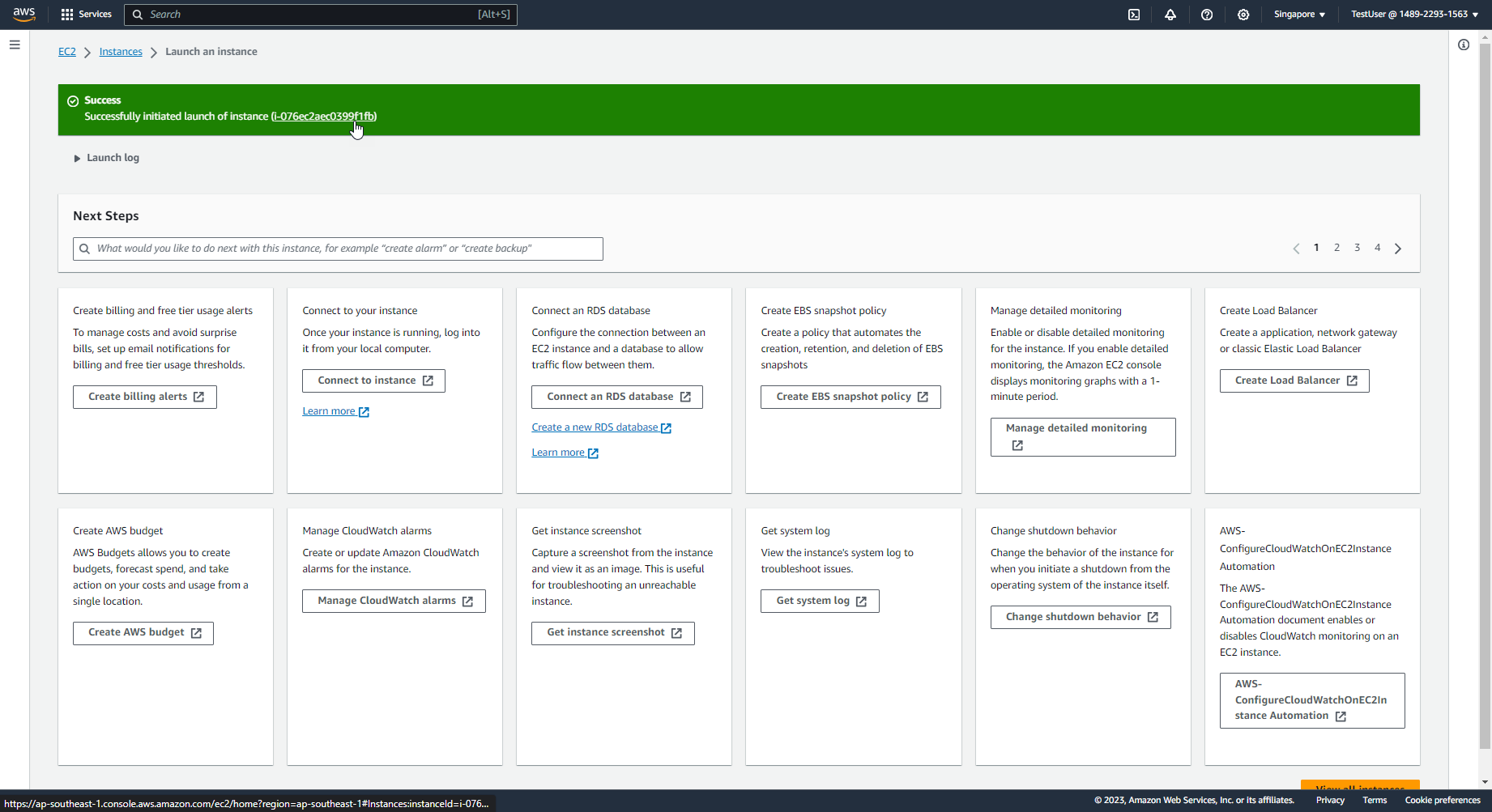
- Congratulations, you have successfully created EC2 with instance type t3.small
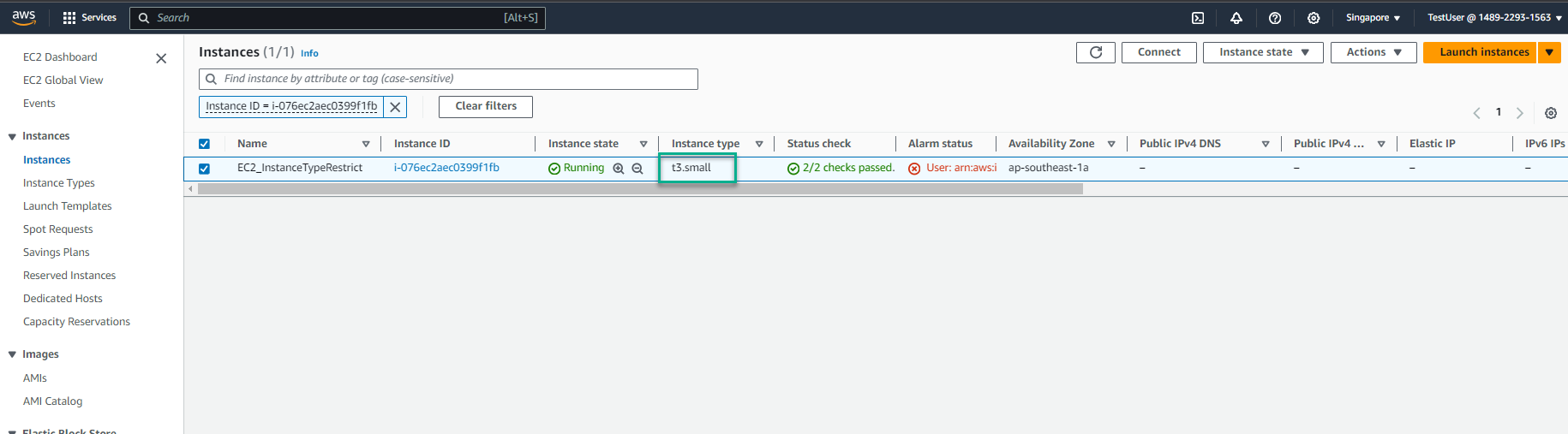
-
Check Permissions policies for Instance type: m5.4xlarge
- Select Launch instance
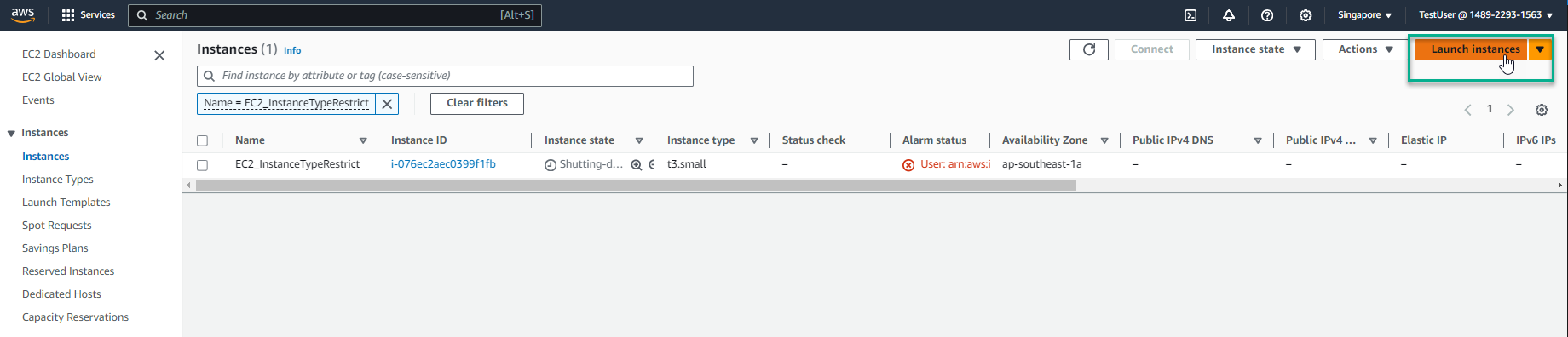
- In the Name section, enter
EC2_m5.4xlarge
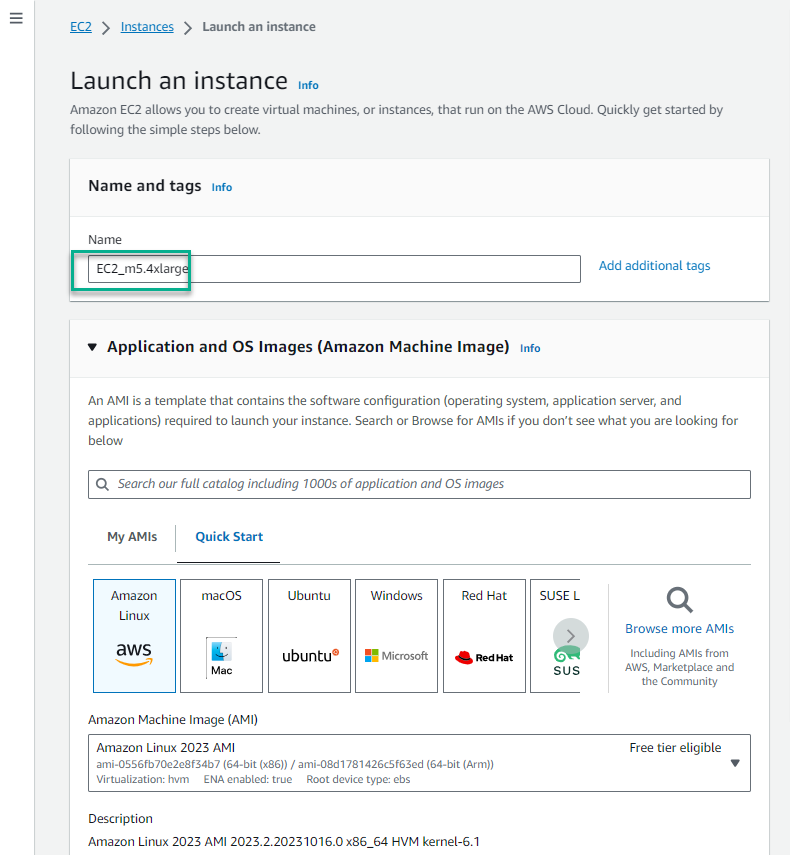
- In the Architecture section, keep the value 64-bit(x86)
- In the Instance type section, select the triangle symbol, select
m5.4xlarge
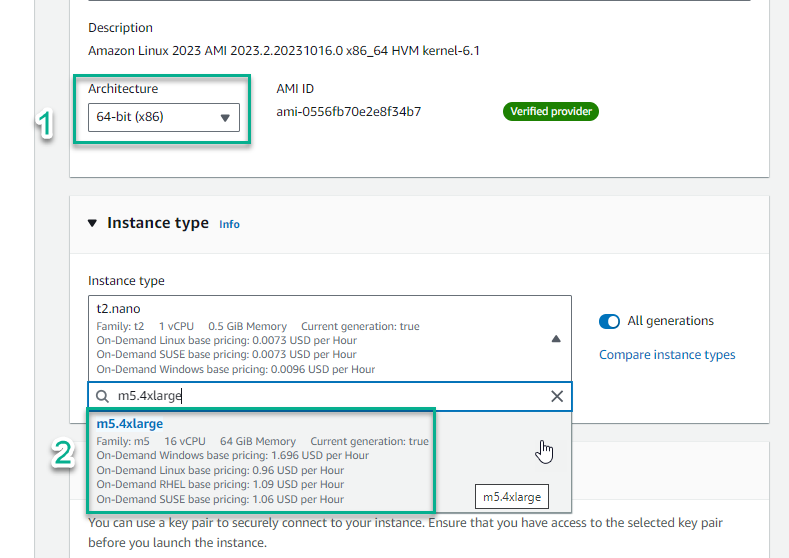
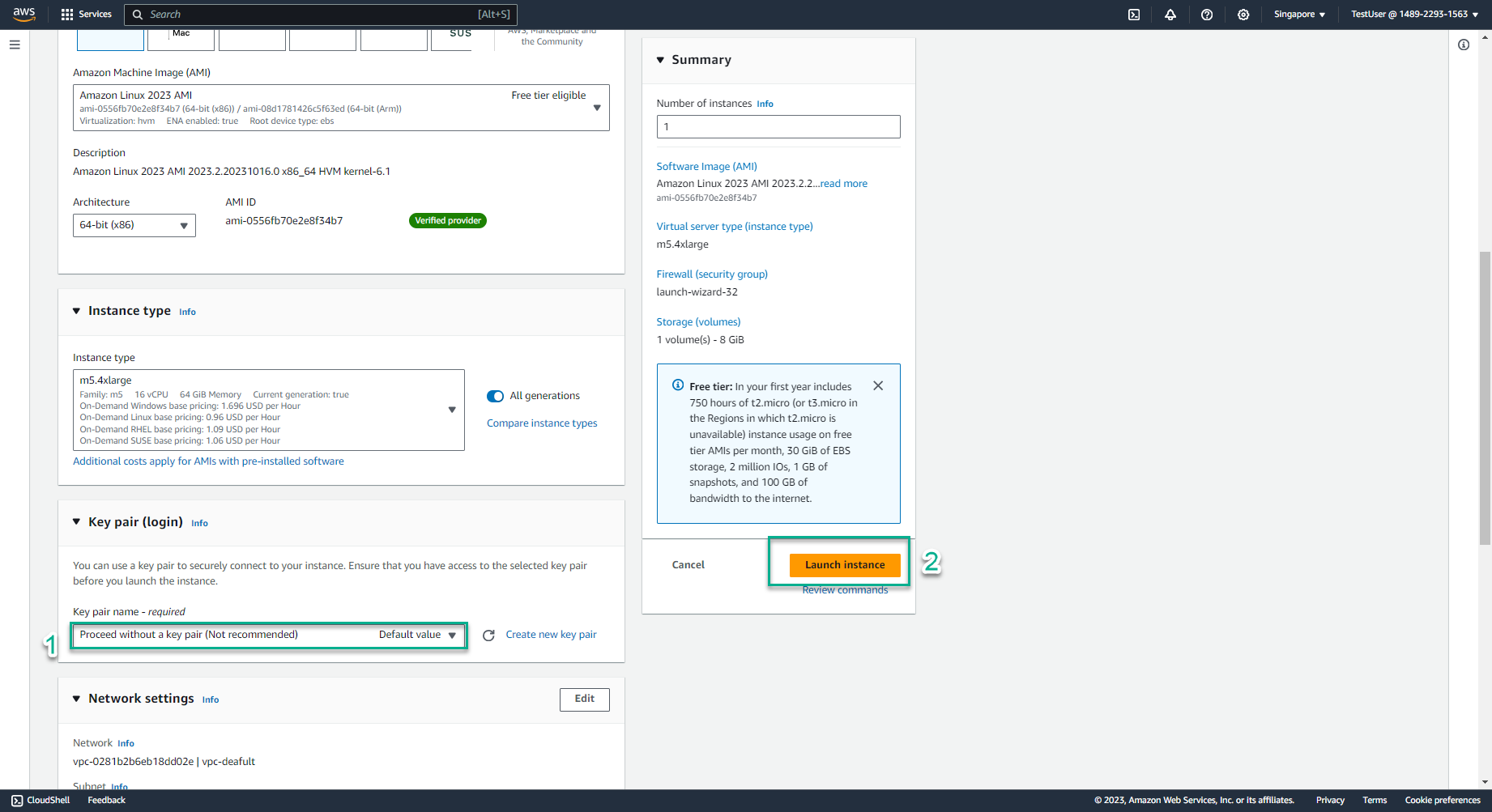
- In the key pair name section, select the triangle symbol, select Proceed without a key pair (Not recommended)
- Select Launch instance
- You received the response Instance launch failed - because you are not authorized. This satisfies the permission policy: EC2_InstanceTypeRestrict that you created in step 3.
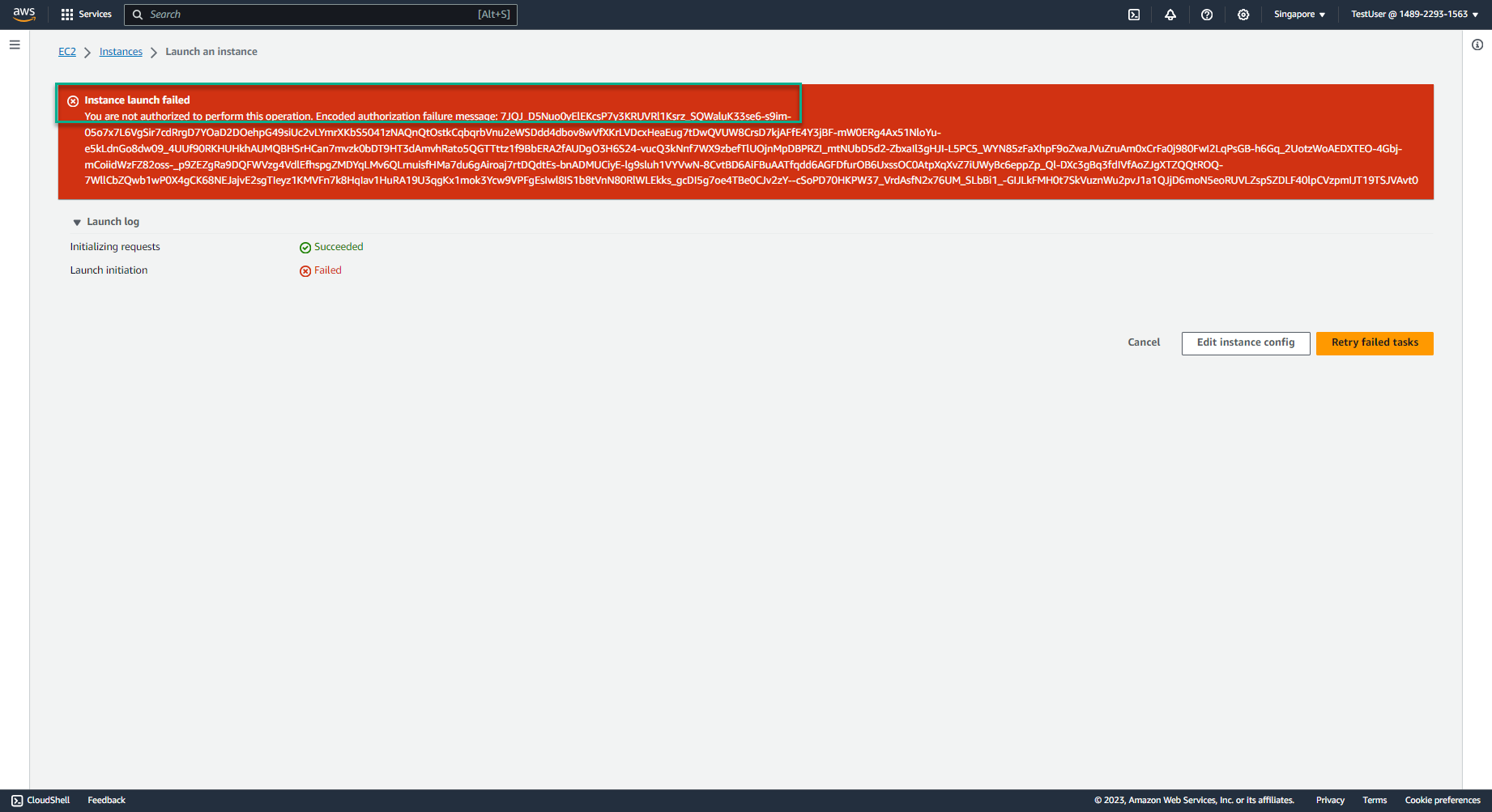
-
You can proceed to step 3 again, creating EC2 with instance type t3.large to check the effectiveness of the permission policy: EC2_InstanceTypeRestrict