Restricting Service Usage by AWS Region
Implementing Region-Based Access Controls for Cost Governance
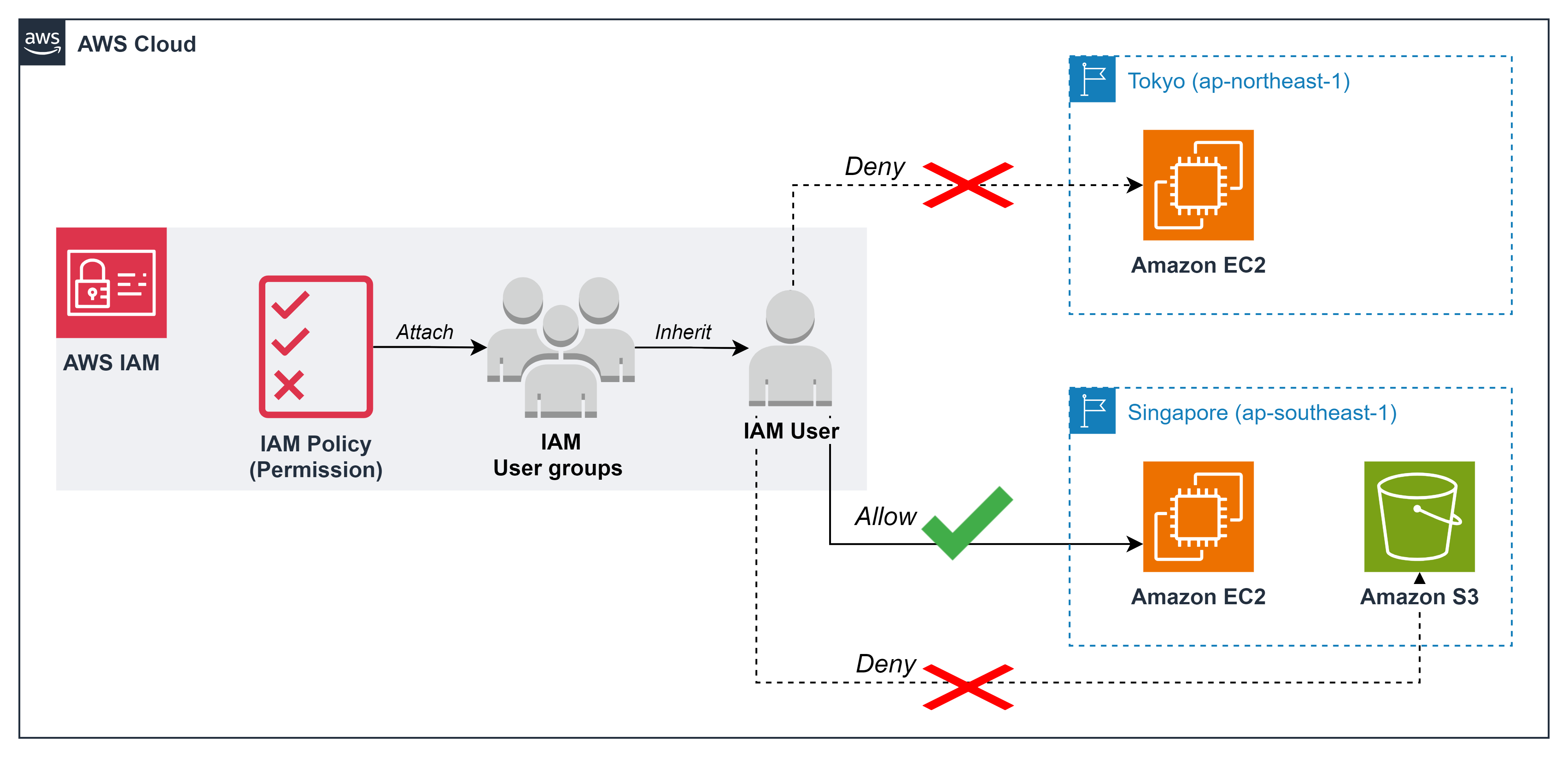
ℹ️ Information: AWS Identity and Access Management (IAM) allows you to implement fine-grained access controls that restrict service usage to specific AWS Regions, helping organizations control costs by limiting where resources can be deployed.
Business Benefits of Region Restrictions
- Centralizes resource deployment to optimize costs
- Reduces data transfer fees between regions
- Improves application performance by placing resources closer to end users
- Simplifies compliance with data residency requirements
- Enhances security by limiting the geographic scope of potential resource creation
For example, if your end users are primarily located in Vietnam, deploying resources in the Singapore Region (ap-southeast-1) provides lower latency and reduced data transfer costs compared to more distant AWS Regions.
⚠️ Warning: This lab requires at least two IAM Users to demonstrate the implementation and testing of region-based restrictions. If you haven’t created IAM Users previously, refer to the lab: Access Rights Management with AWS IAM.
Implementation Steps
-
Create a Region Restriction Policy
- Navigate to the IAM console by entering
IAMin the AWS Management Console search box - Select IAM service
- In the navigation pane, select Policies
- Click Create policy
- Switch to the JSON editor tab instead of using the visual editor
- Delete any existing template code in the editor
- Copy and paste the following policy document, then click Next:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": "ec2:*", "Resource": "*", "Condition": { "StringEquals": { "aws:RequestedRegion": "ap-southeast-1" } } } ] }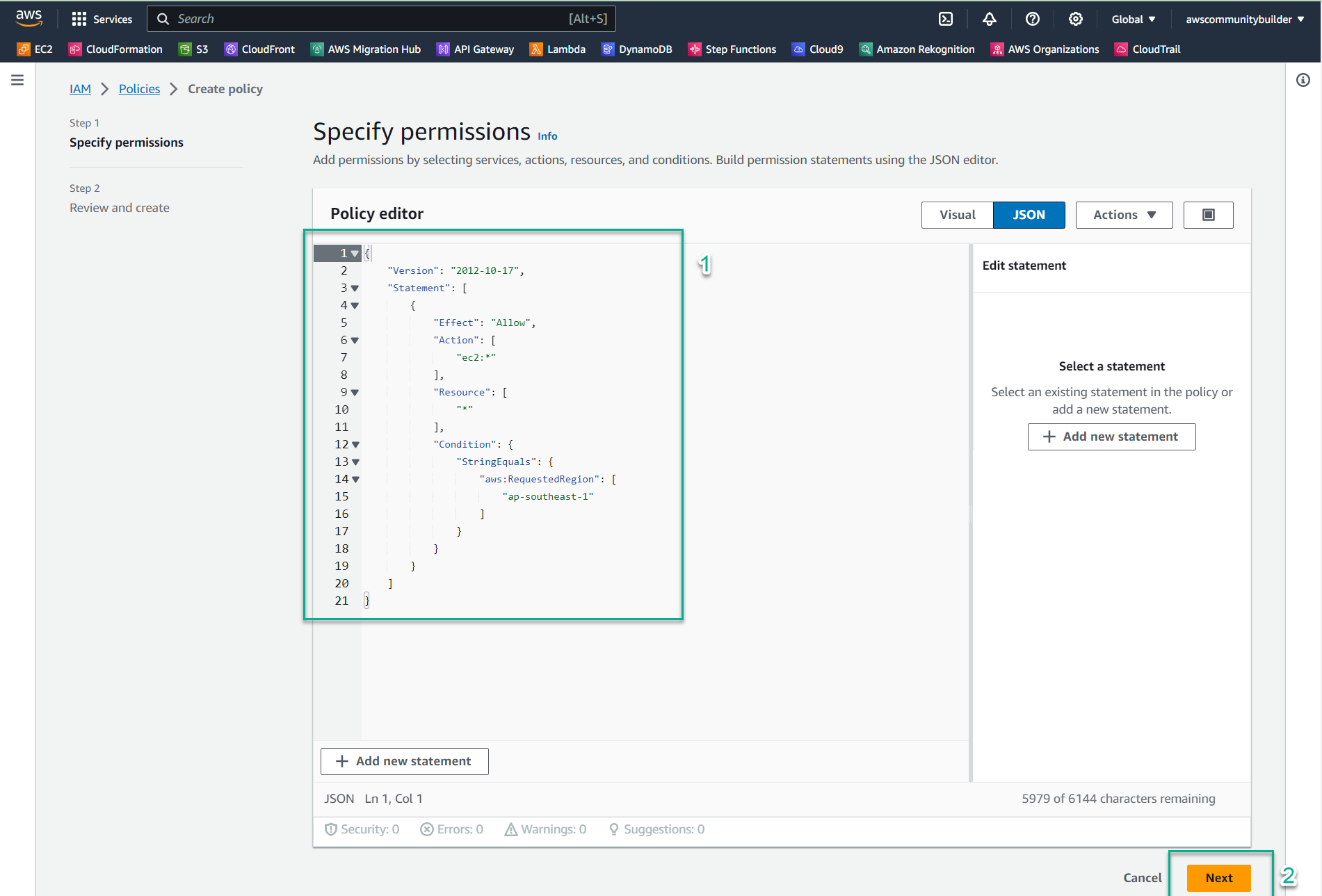
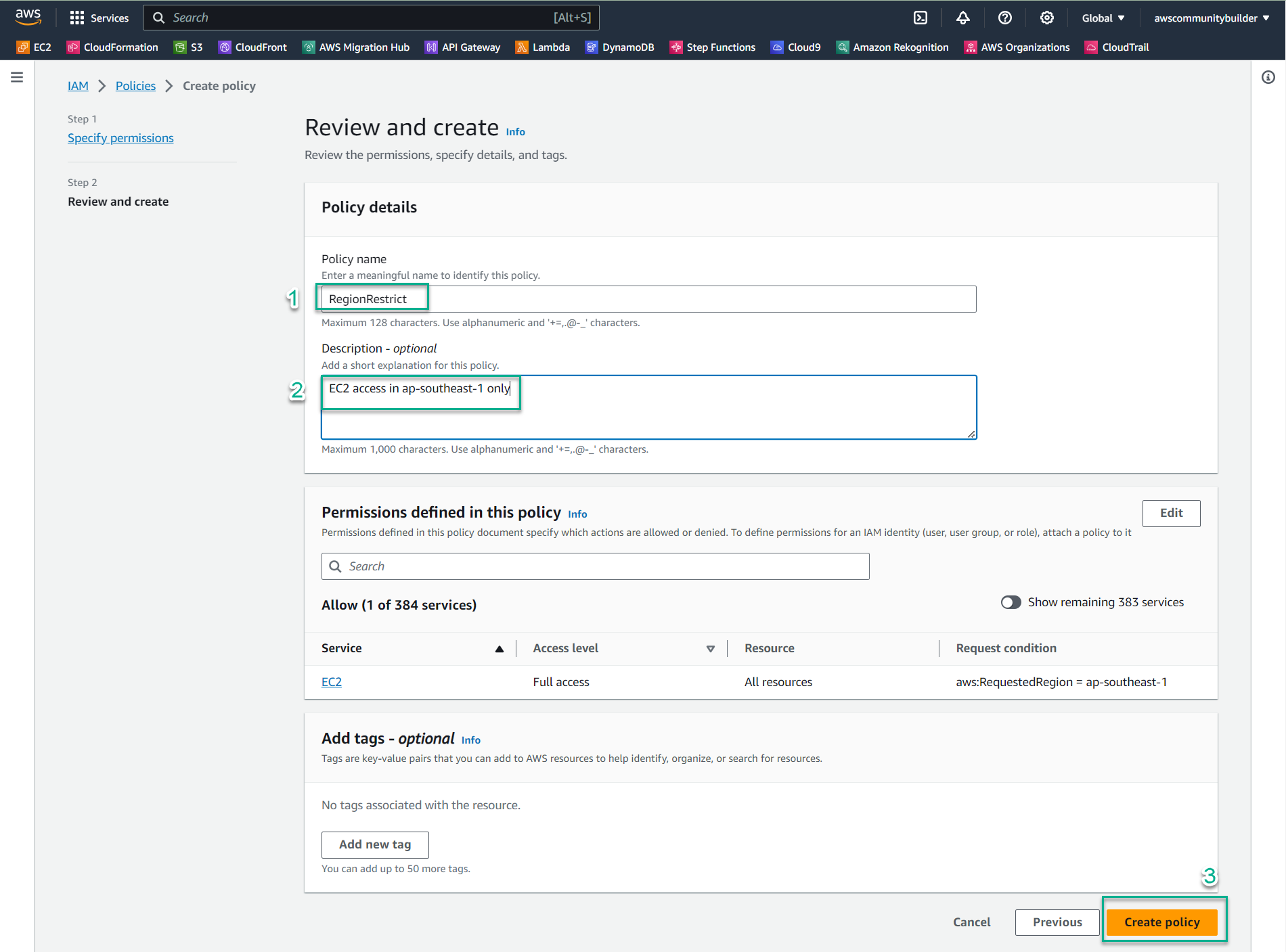
- Enter the following details:
- Policy name:
RegionRestrict - Description:
EC2 access in ap-southeast-1 only
- Policy name:
- Click Create policy
💡 Pro Tip: This policy grants full EC2 permissions (
ec2:*) but only when the requested region is Singapore (ap-southeast-1). Any EC2 actions attempted in other regions will be denied. - Navigate to the IAM console by entering
-
Create an IAM Group for Cost Management
- In the IAM console, select User groups
- Click Create group
- For User group name, enter
CostTest
- In the Attach permissions policies section, search for
RegionRestrict - Select the checkbox next to the policy you created in step 1
- Click Create group
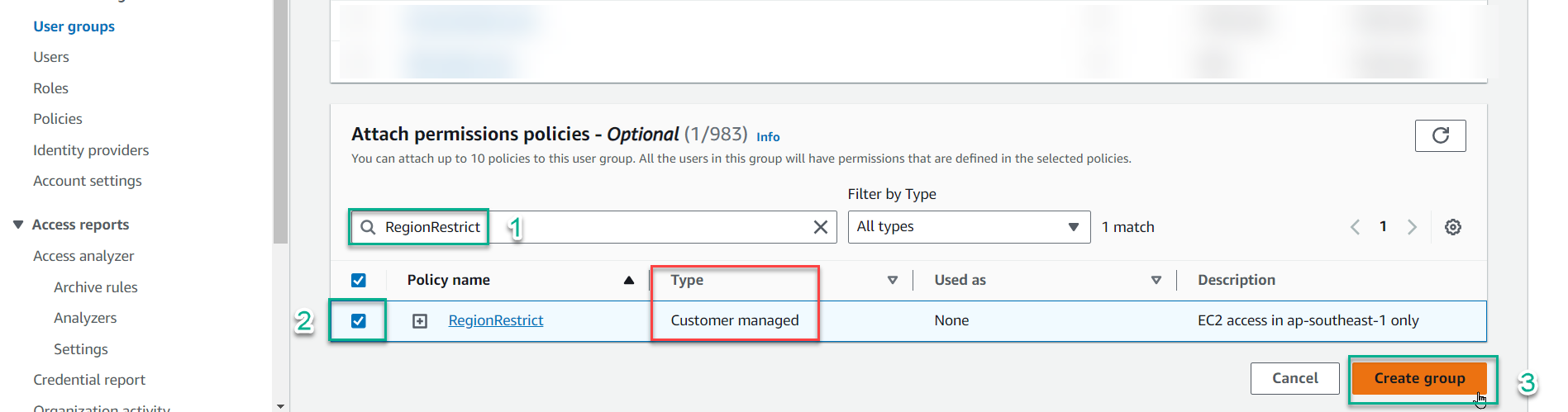
ℹ️ Information: Notice that your policy appears as Customer managed in the Type column, indicating it was created by you and can be edited. AWS managed policies (created and maintained by AWS) cannot be modified.
-
Create a Test User
- In the IAM console, select Users
- Click Create user
- Configure the user with these settings:
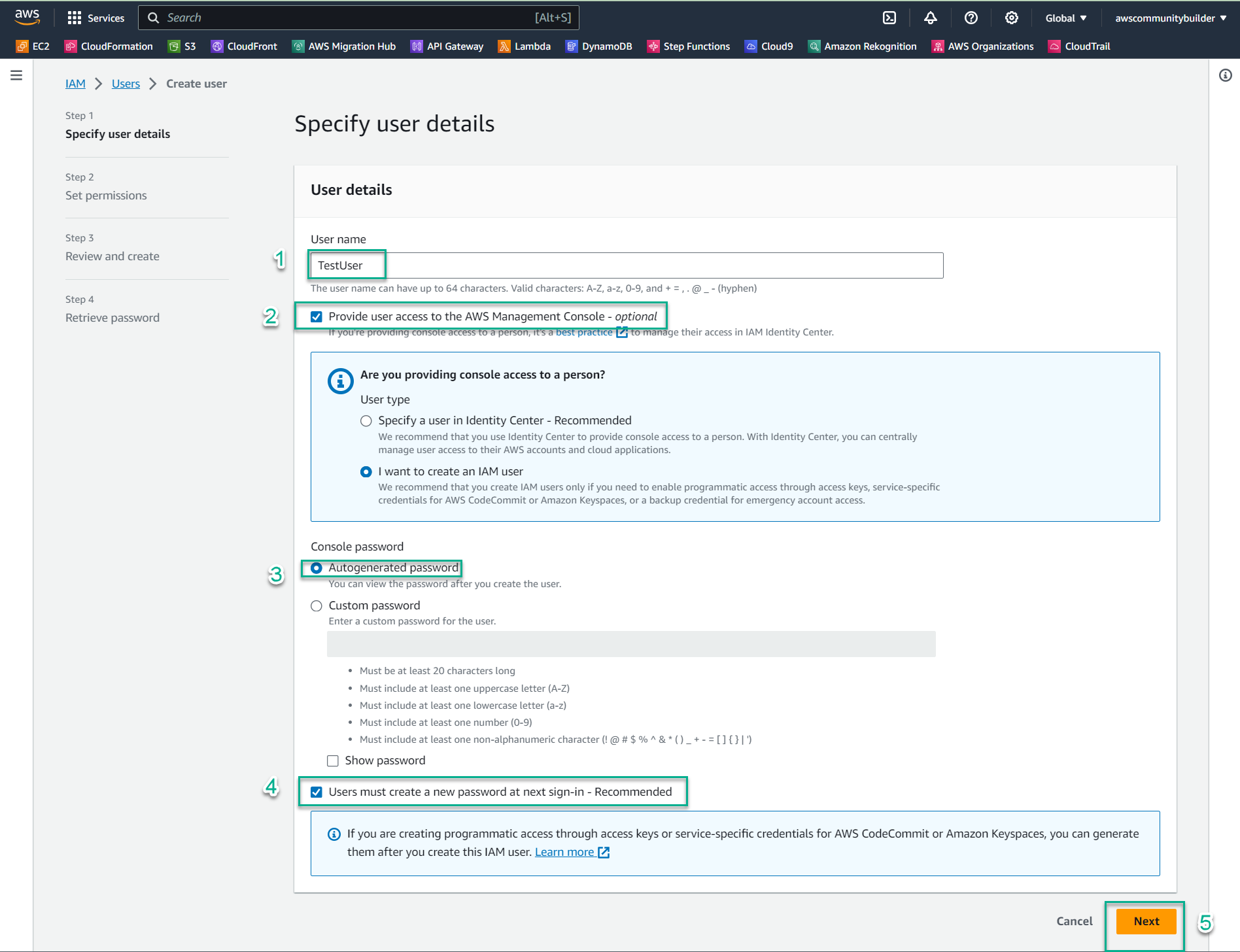
- User name:
TestUser - Select Provide user access to the AWS Management Console
- Select I want to create an IAM user
- Select Autogenerated password
- Check Users must create a new password at next sign-in
- User name:
- Click Next
🔒 Security Note: As a cloud administrator, following these steps ensures you don’t know the password for IAM users you create. This enforces the principle of least privilege by requiring users to set their own passwords and take responsibility for their AWS account interactions.
- Under Permissions options, select Add user to group
- Select the CostTest group you created in step 2
- Click Next
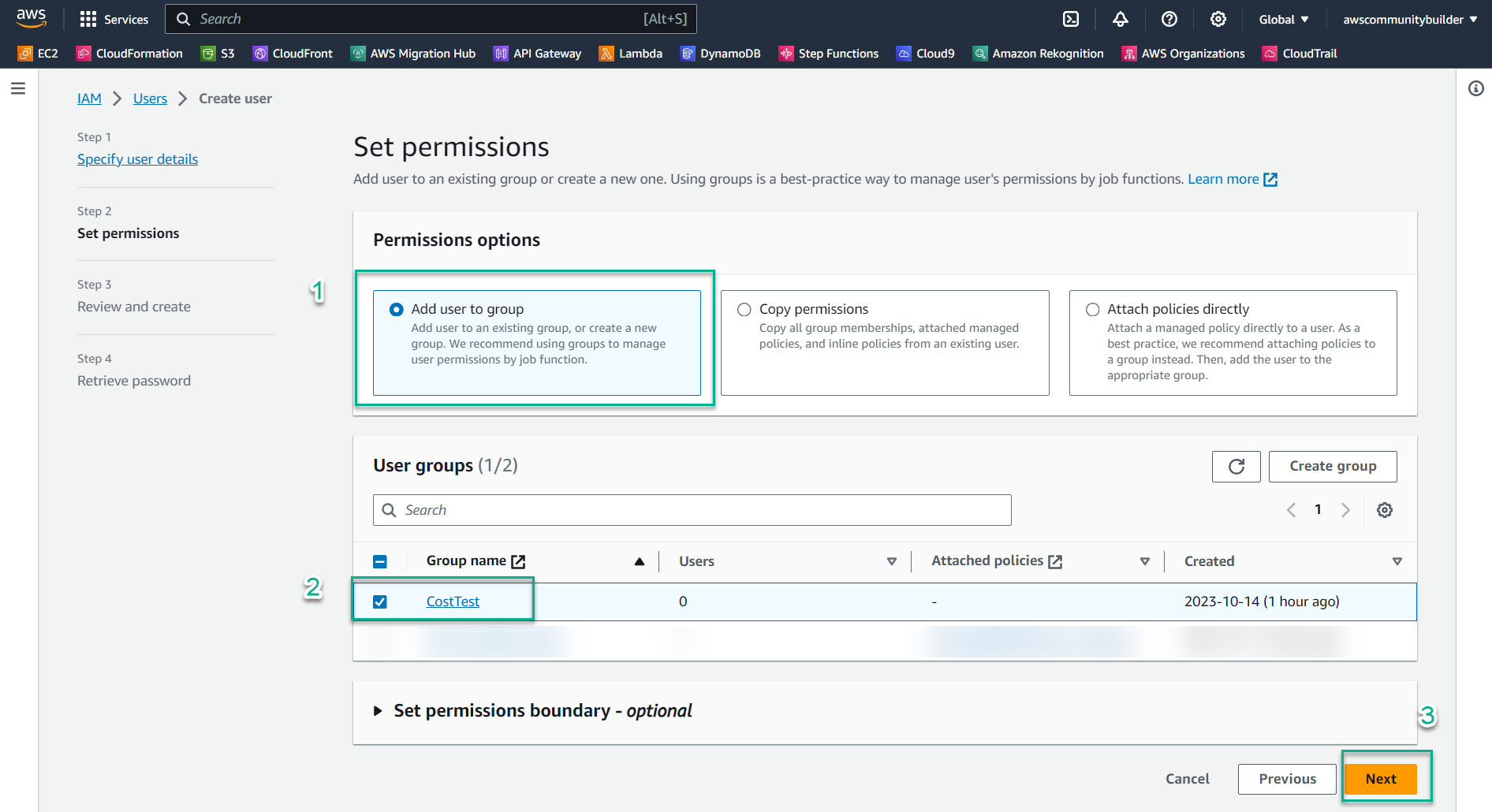
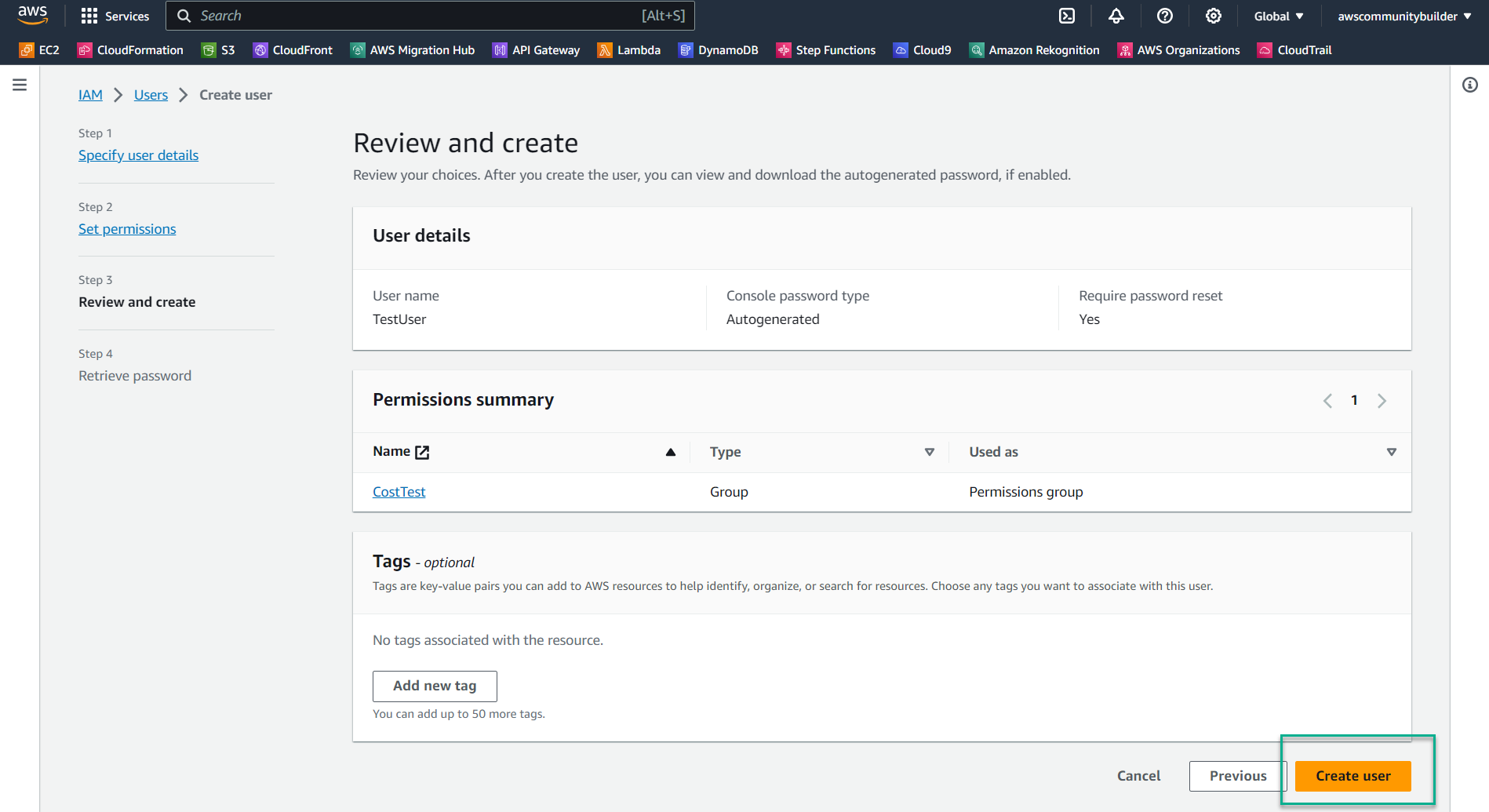
- Review the configuration and click Create user
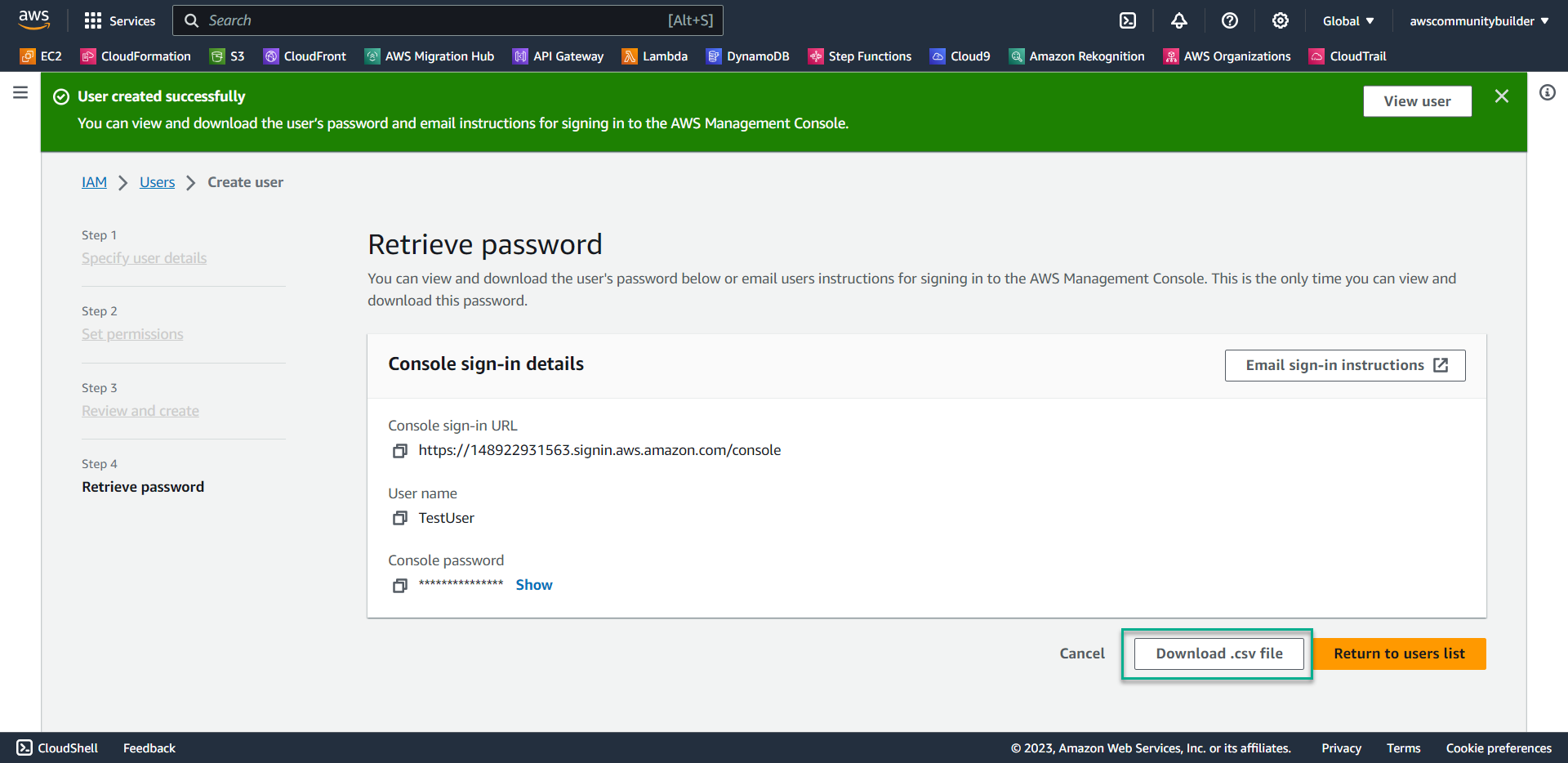
- On the confirmation page, click Download .csv file to save the login credentials
💡 Pro Tip: Adding users to groups follows AWS best practices for centralized permission management. This approach simplifies administration by allowing you to add or remove permissions for multiple users simultaneously, reducing the risk of permission inconsistencies.
-
Test EC2 Access in the Singapore Region
- Sign in using the TestUser credentials you downloaded
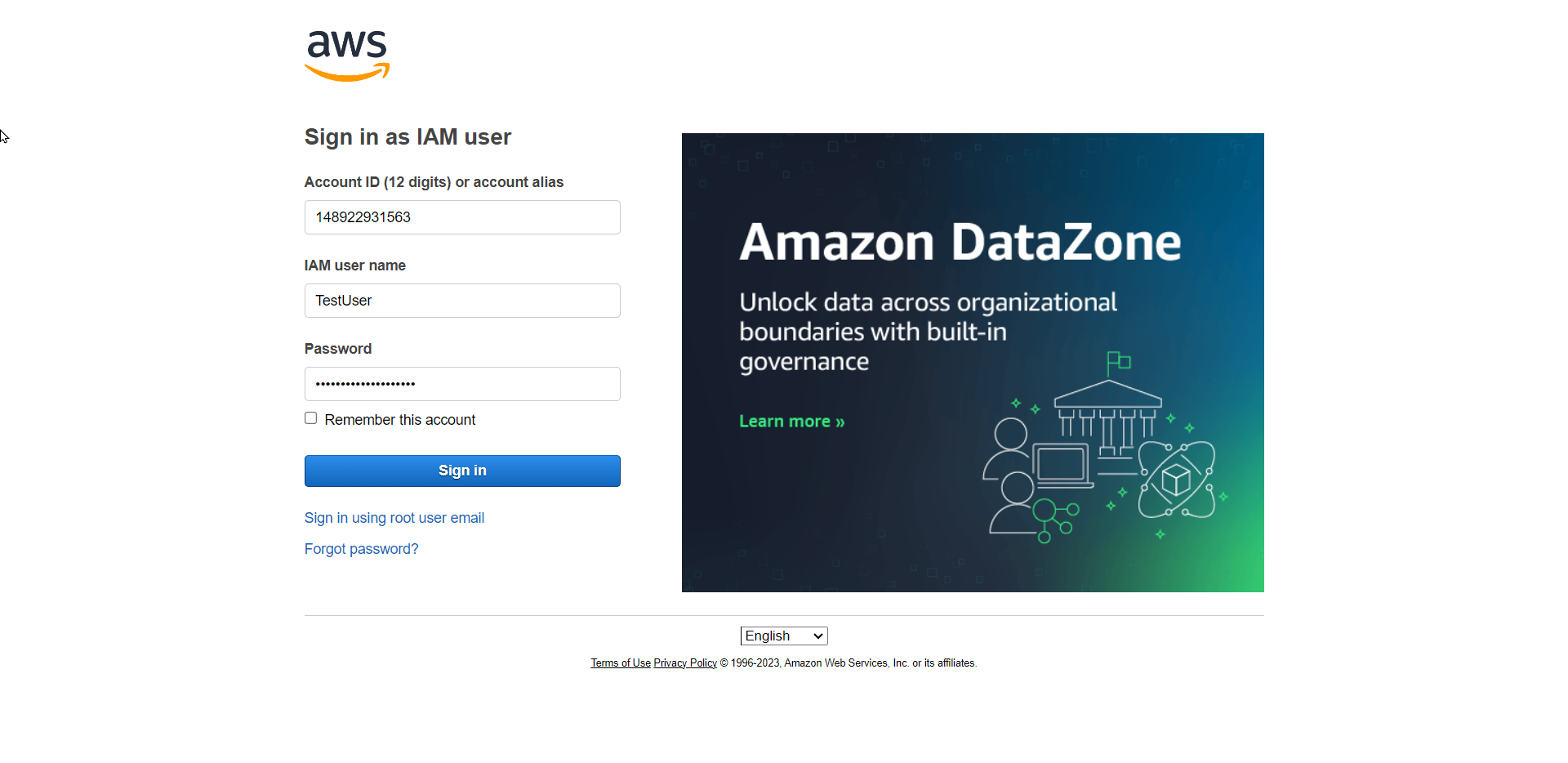
- Set a new password as prompted
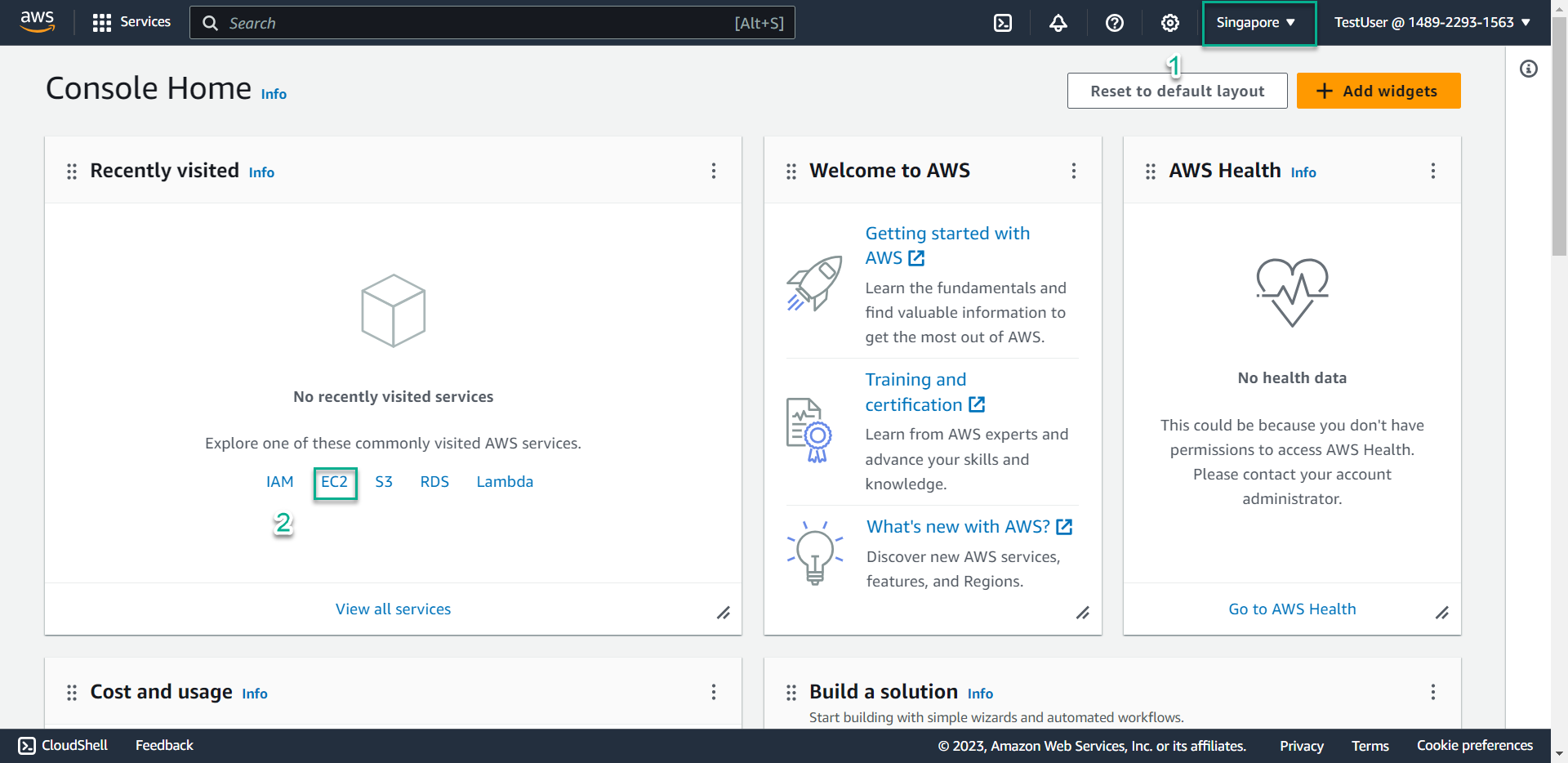
- Verify you’re in the Singapore region, then navigate to the EC2 service
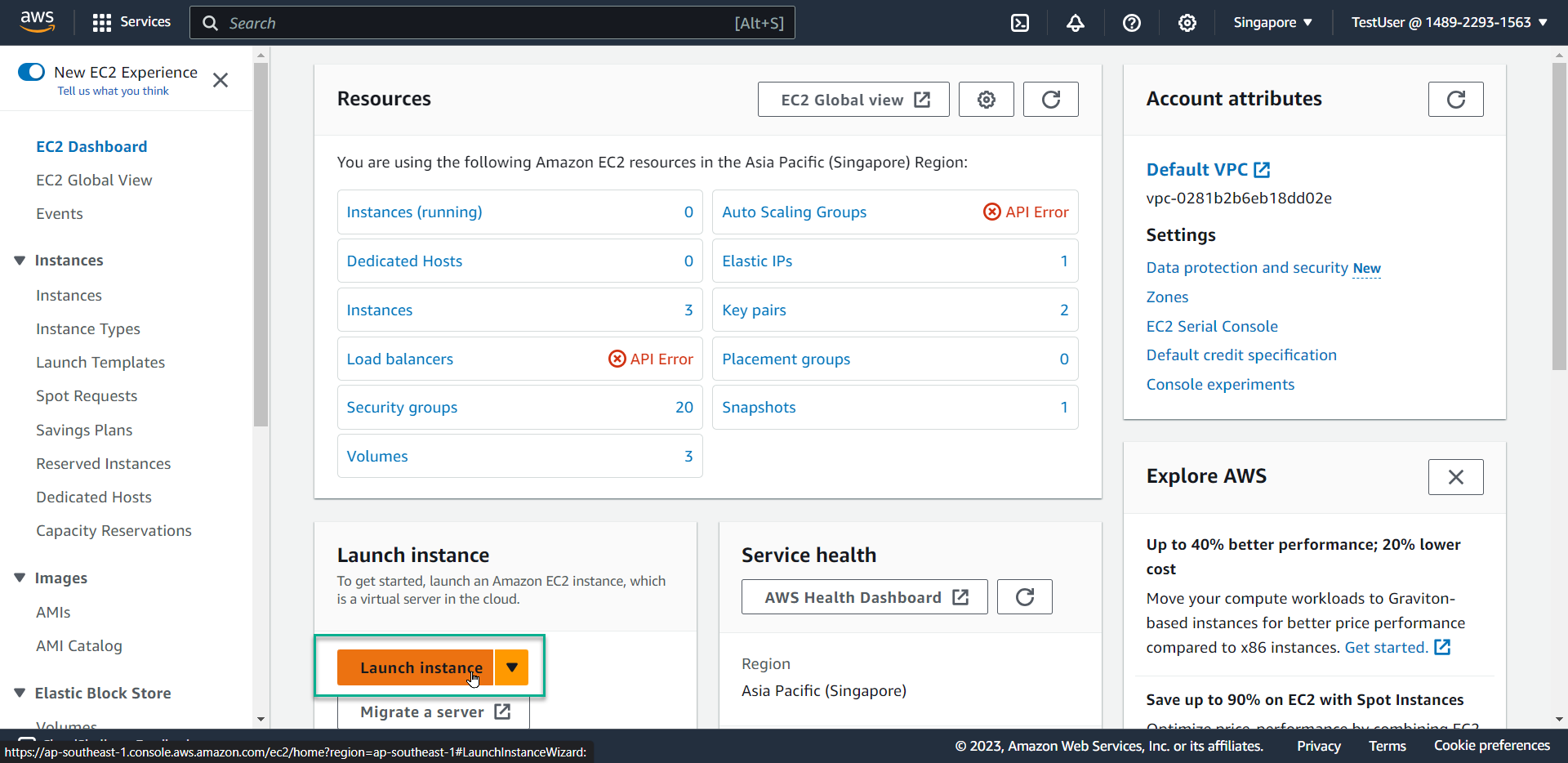
- Click Launch instance
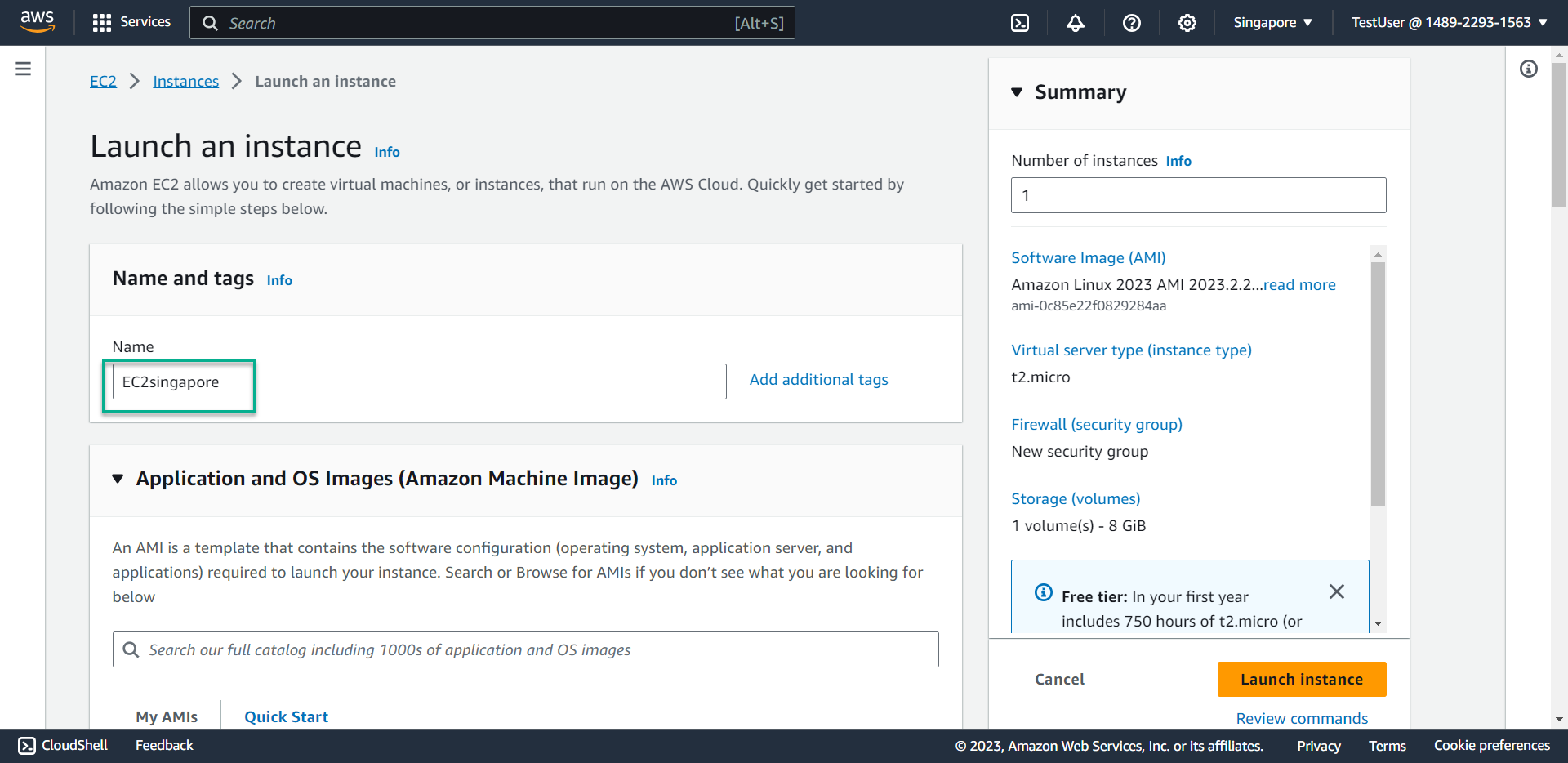
- Enter
EC2singaporeas the instance name
- In the Key pair section, click the dropdown arrow
- Select Proceed without a key pair
- Click Launch instance
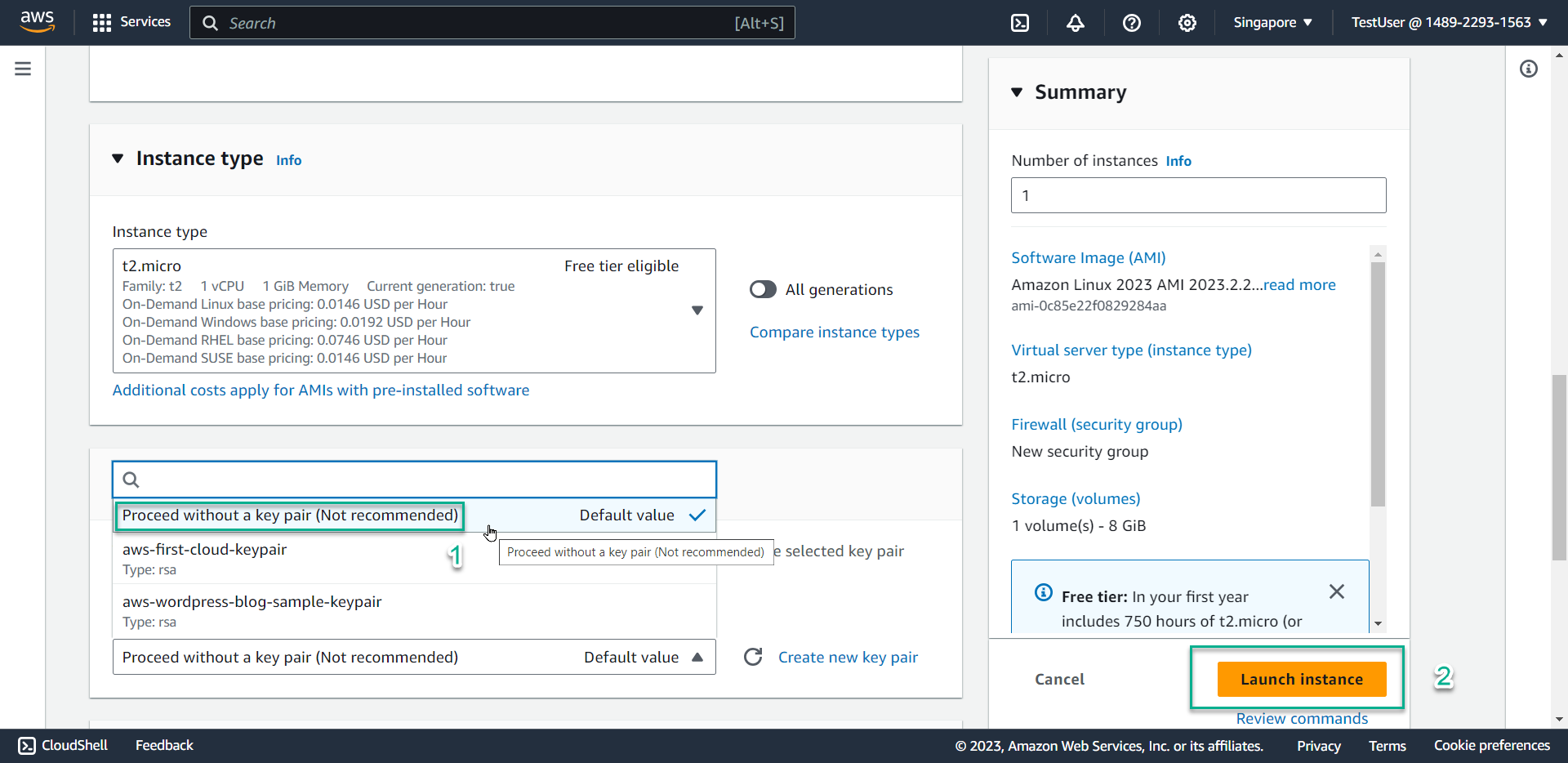
ℹ️ Information: In a production environment, you would create or select an existing key pair to enable secure SSH access to your instance. For this test, we’re only verifying policy effectiveness, so a key pair isn’t necessary.
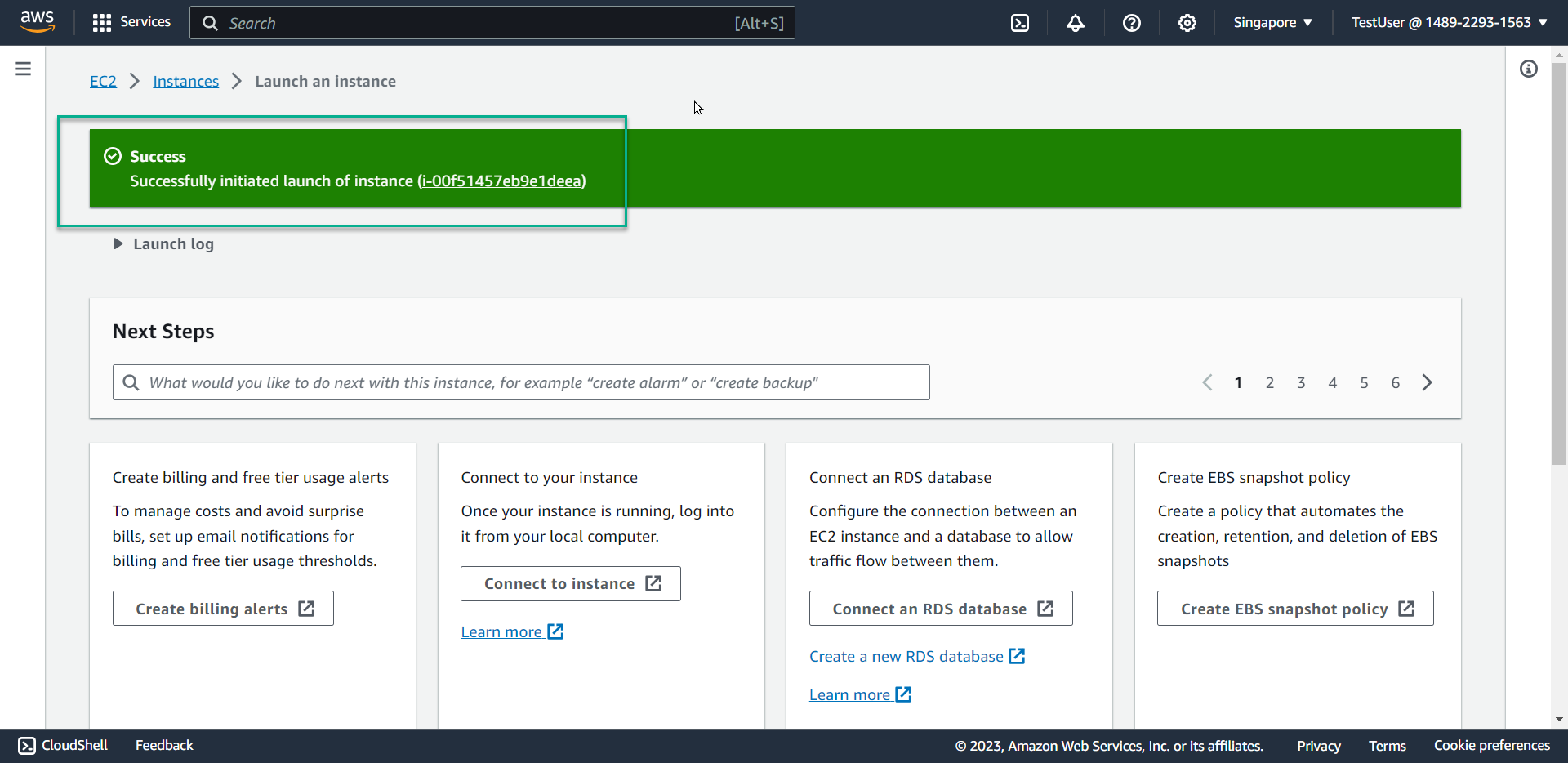
- Result: The EC2 instance is successfully created
-
Verify EC2 Access Denial in the Tokyo Region
- Switch to the Tokyo region
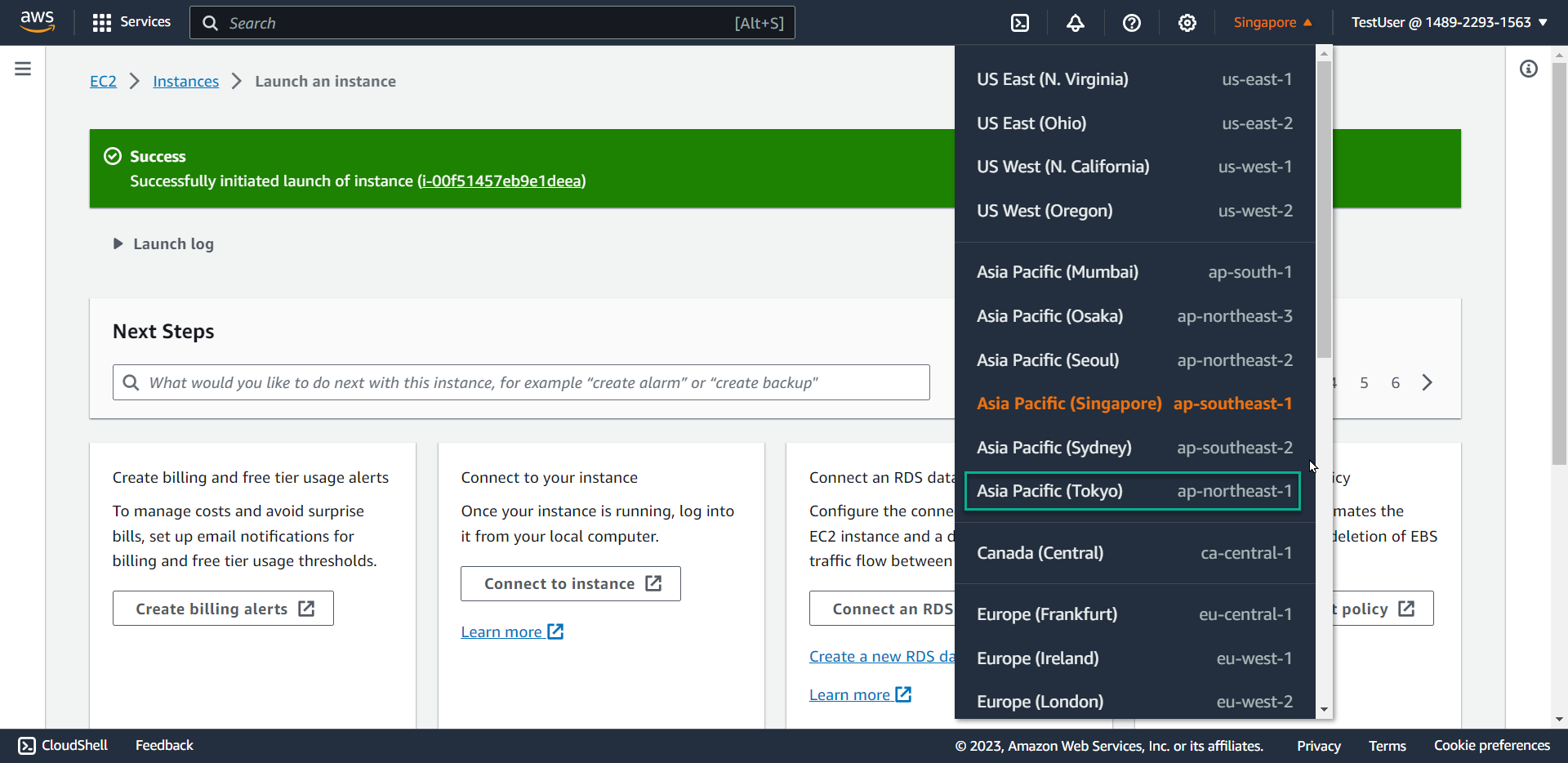
- Attempt to launch an instance named
EC2tokyo
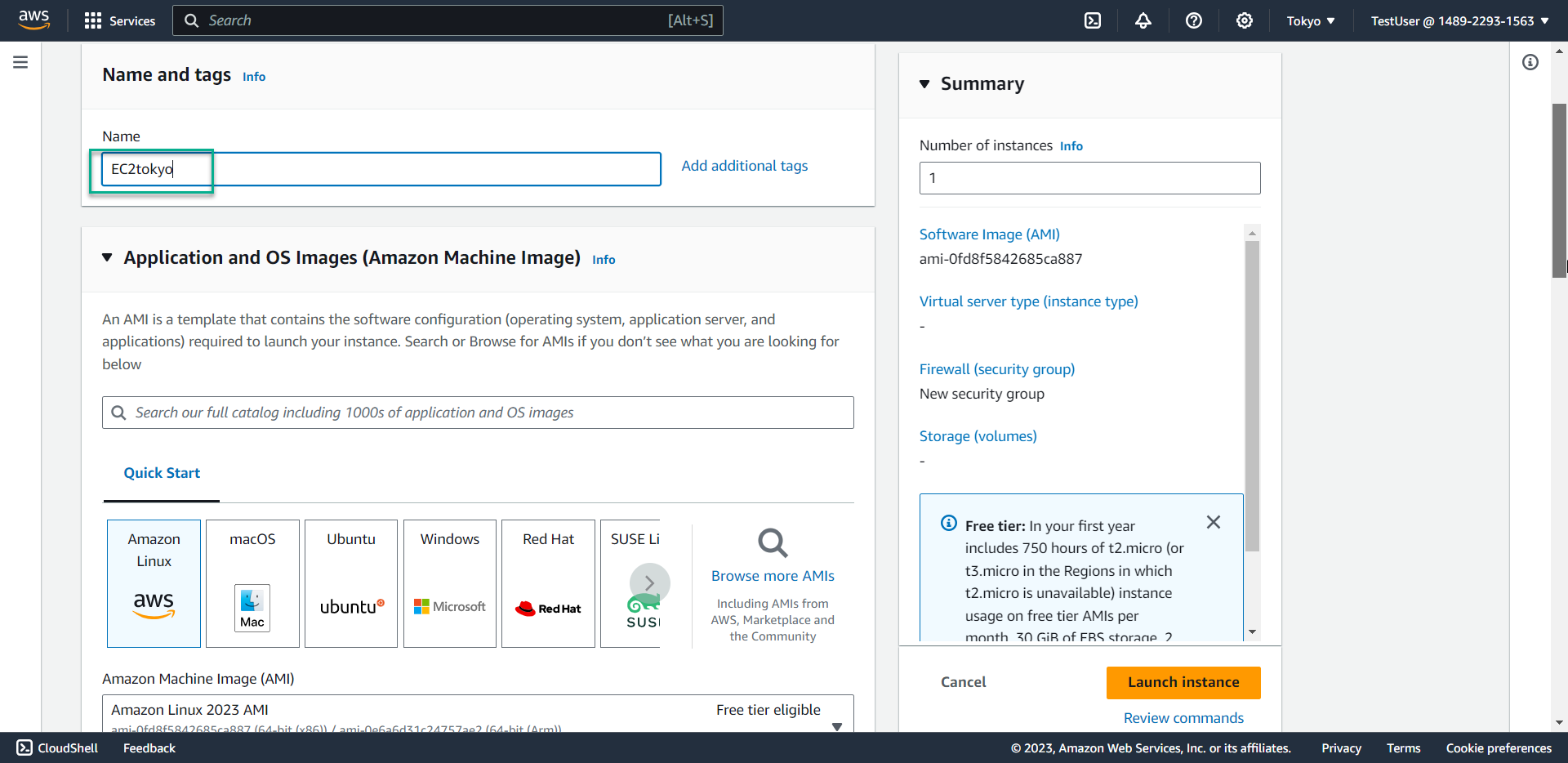
- In the Key pair section, select Proceed without a key pair
- Click Launch instance
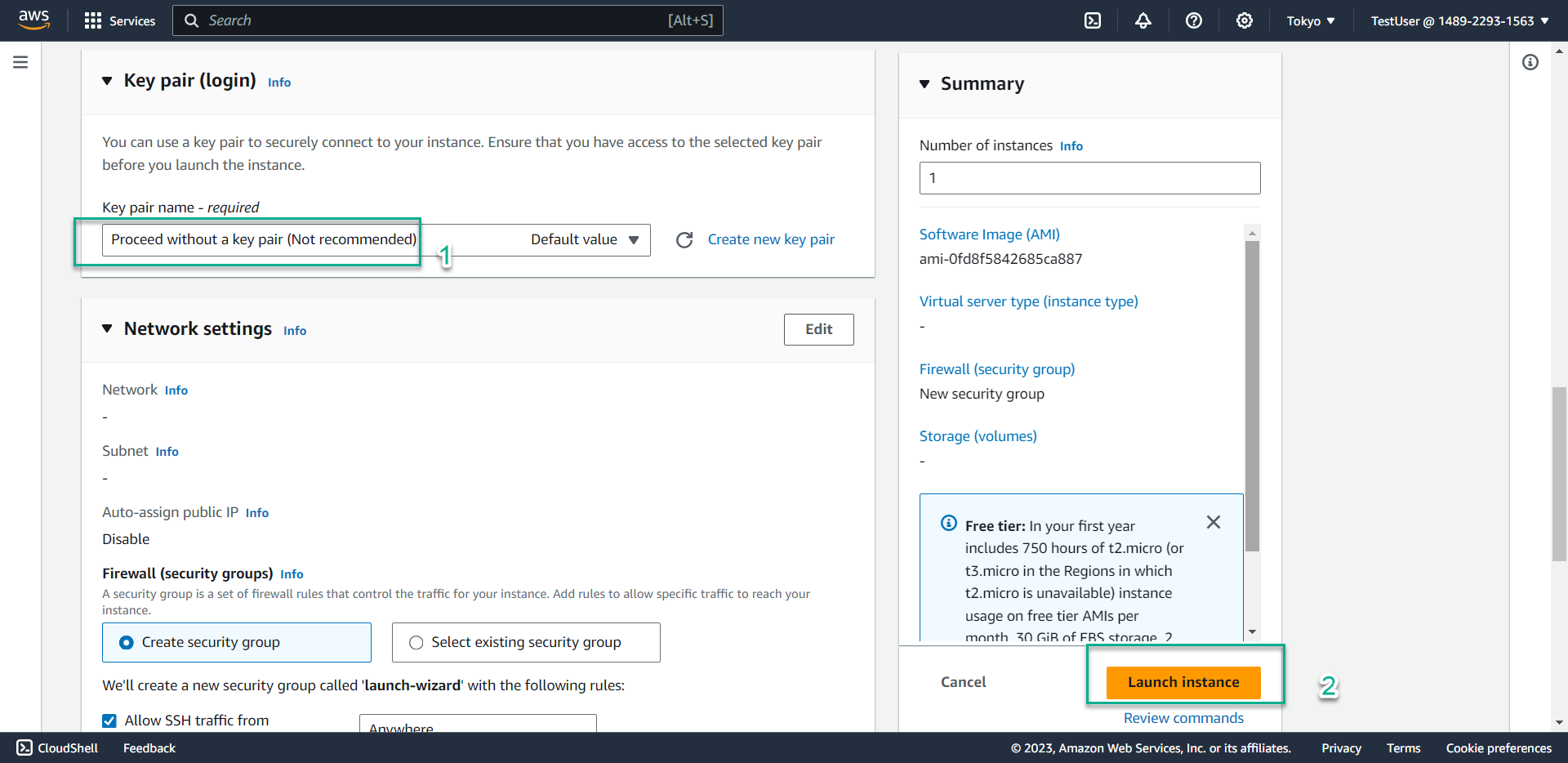
- Result: The instance creation fails due to insufficient permissions
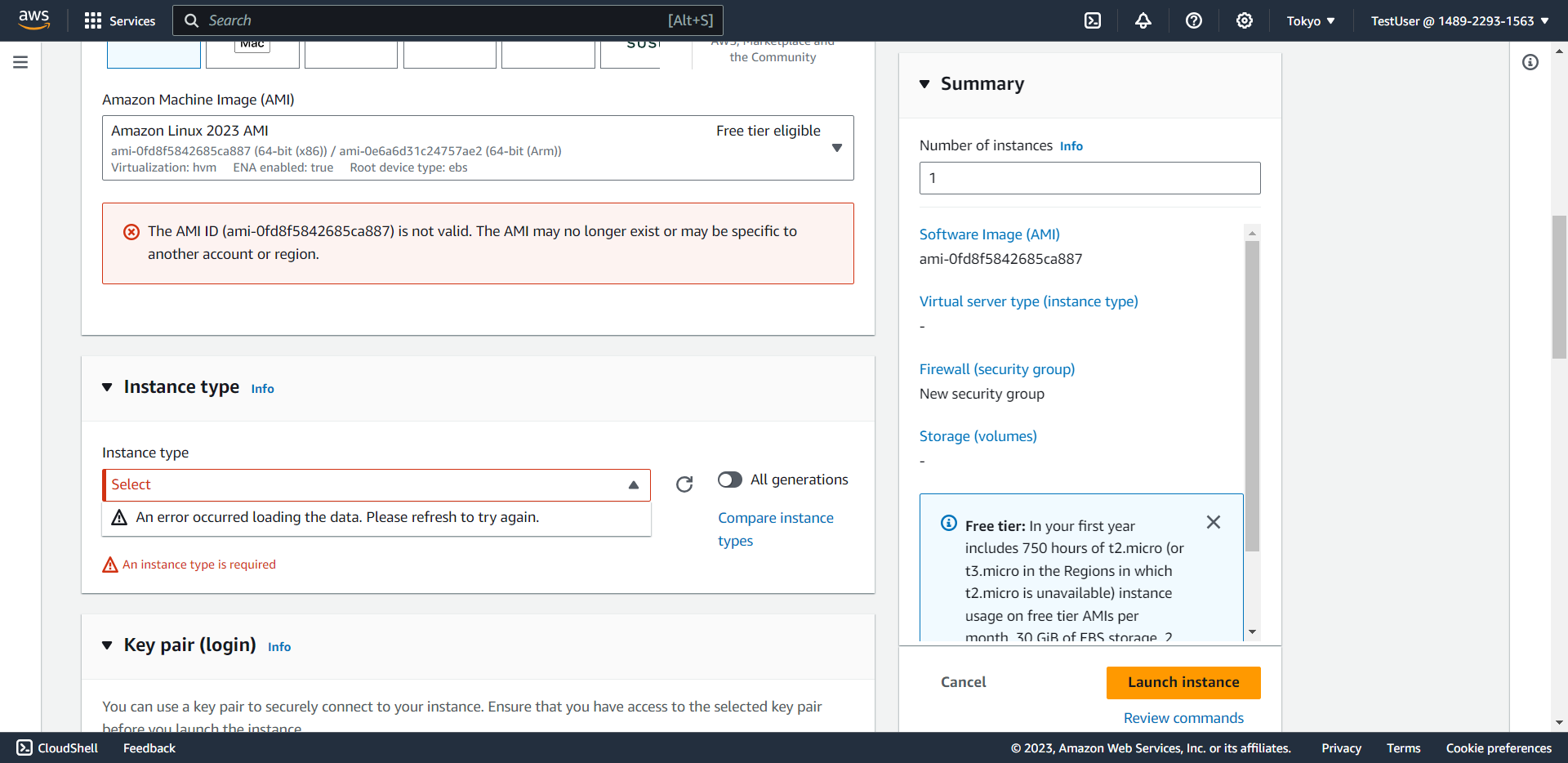
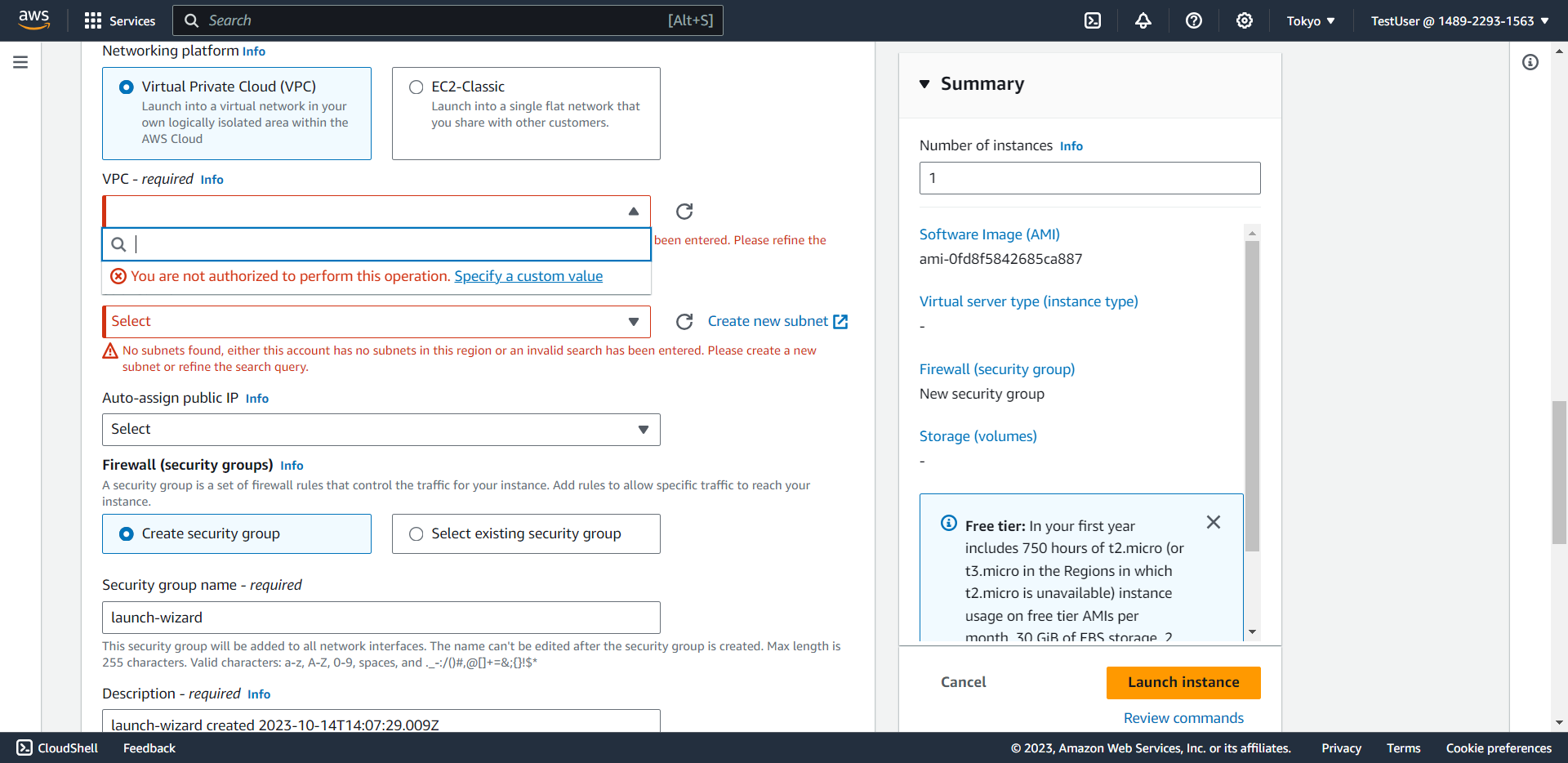
⚠️ Warning: Notice that the interface cannot display AMI ID, instance type, VPC, or subnet information because the policy restricts all EC2 actions in regions other than Singapore.
-
Verify S3 Access Denial in the Singapore Region
- Switch back to the Singapore region
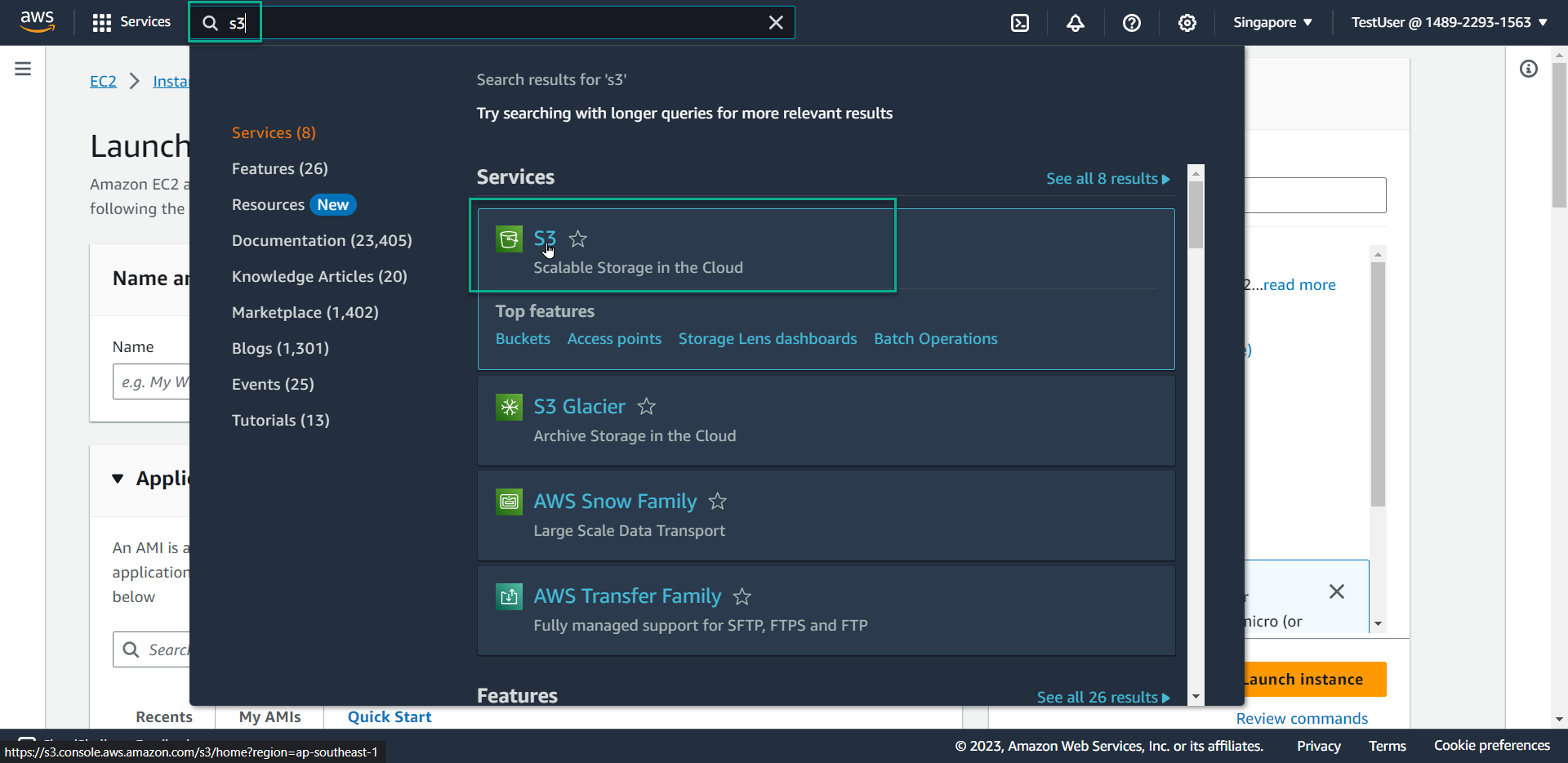
- Search for and select S3 in the console
- Click the navigation menu icon in the left corner
- Select Buckets
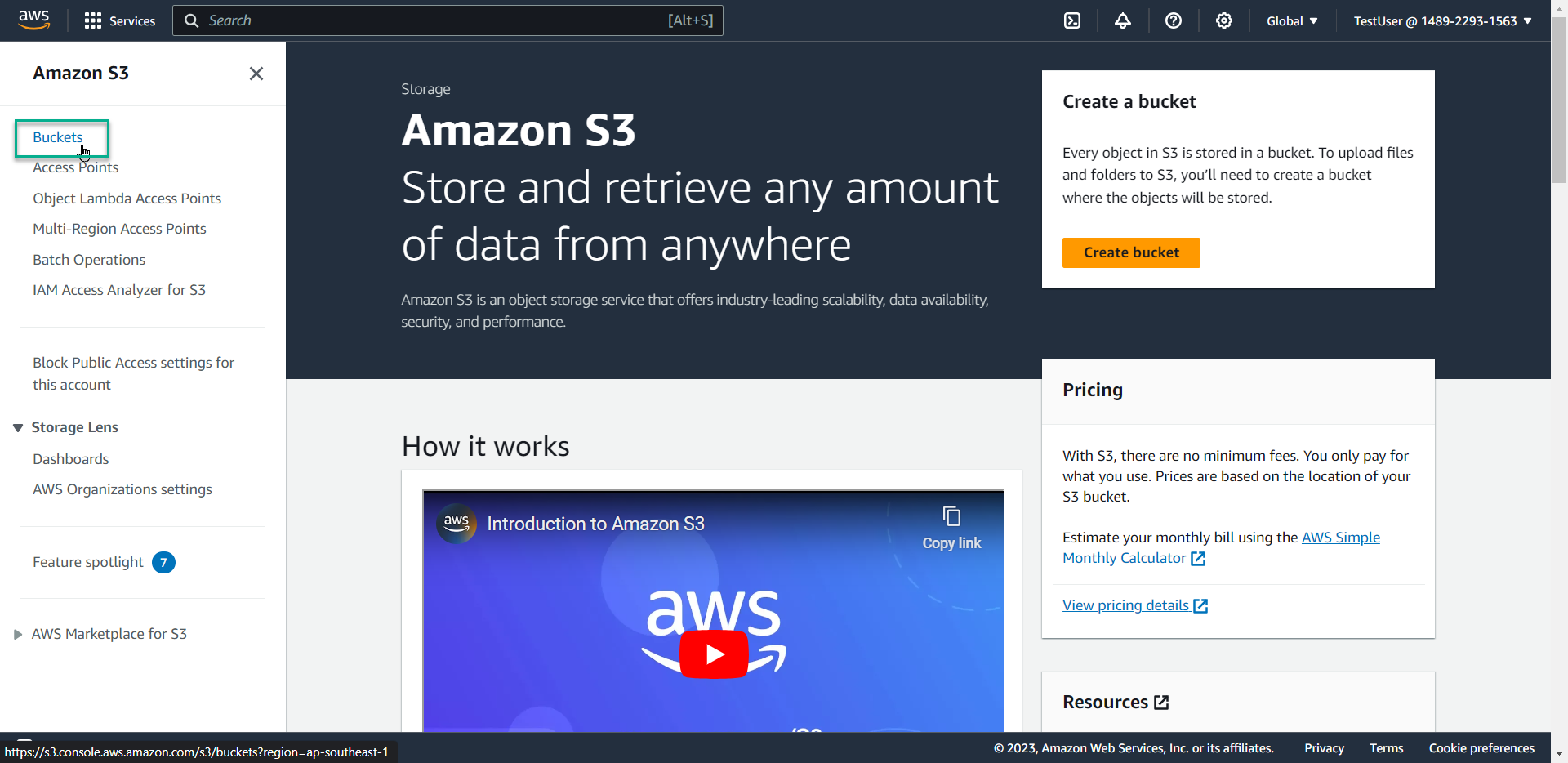
- Result: Access is denied because the policy only grants EC2 permissions, not S3
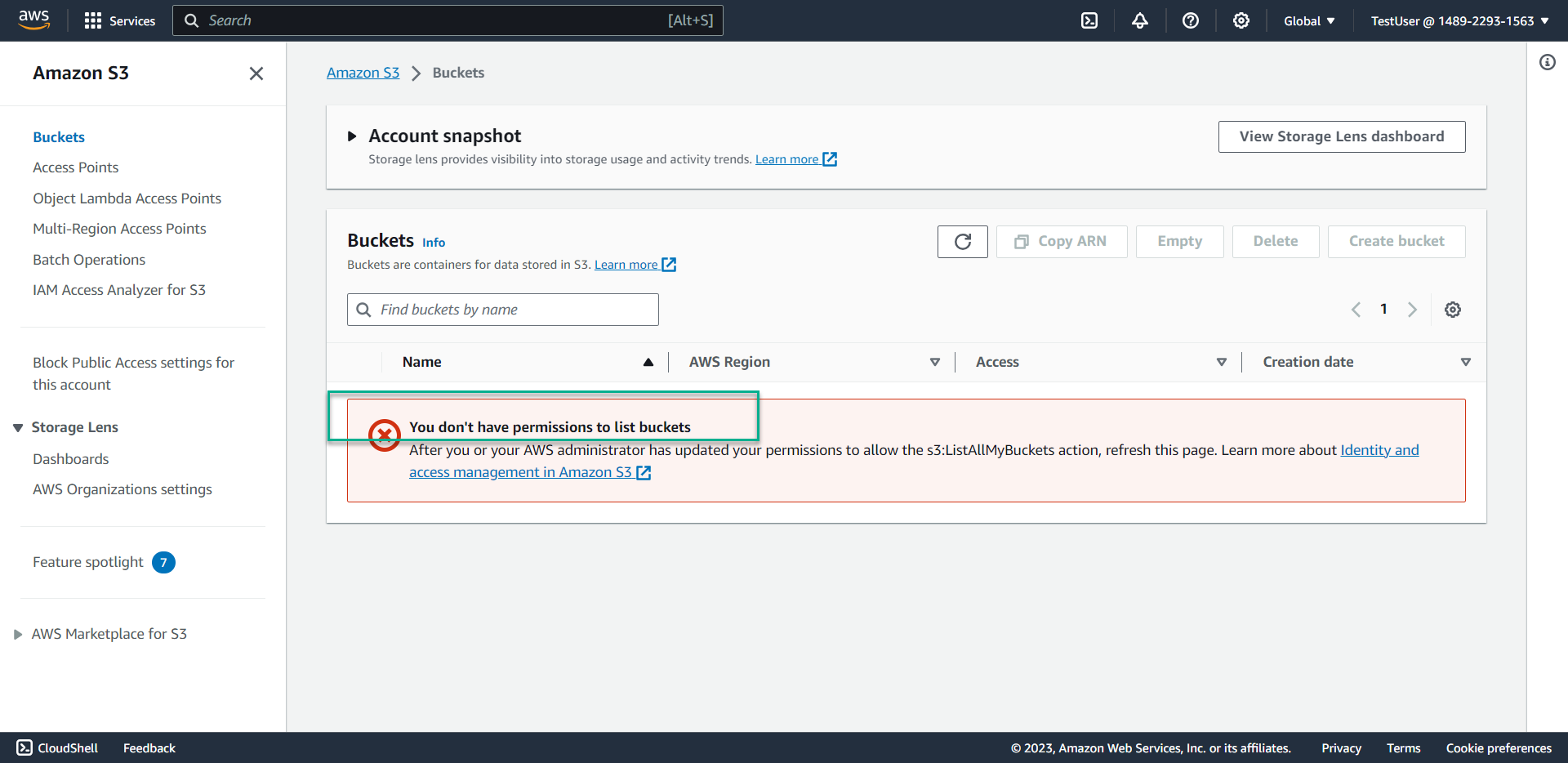
💡 Pro Tip: This demonstrates how IAM policies can be used to implement precise service-level and region-level access controls. Users can only access the specific services and regions explicitly allowed by their assigned policies.
Conclusion
Congratulations! You’ve successfully implemented and tested a region-based access control policy that restricts EC2 usage to the Singapore region only. This approach demonstrates how AWS IAM can be used as an effective cost governance tool by preventing resource deployment in unauthorized regions.